Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Cloud security is a mess these days. Regular security tools don’t cut it anymore, they’re too slow and clunky for systems that change every few minutes. That’s where cloud threat detection comes in handy.
It’s basically a security camera system for your cloud setup, but smarter. It spots the sketchy stuff right away, weird logins, suspicious file changes, configuration mess-ups, and alerts your team before hackers can do real damage.
Wondering how to set this up Cloud Threat Detection Response without losing your mind? Read on.

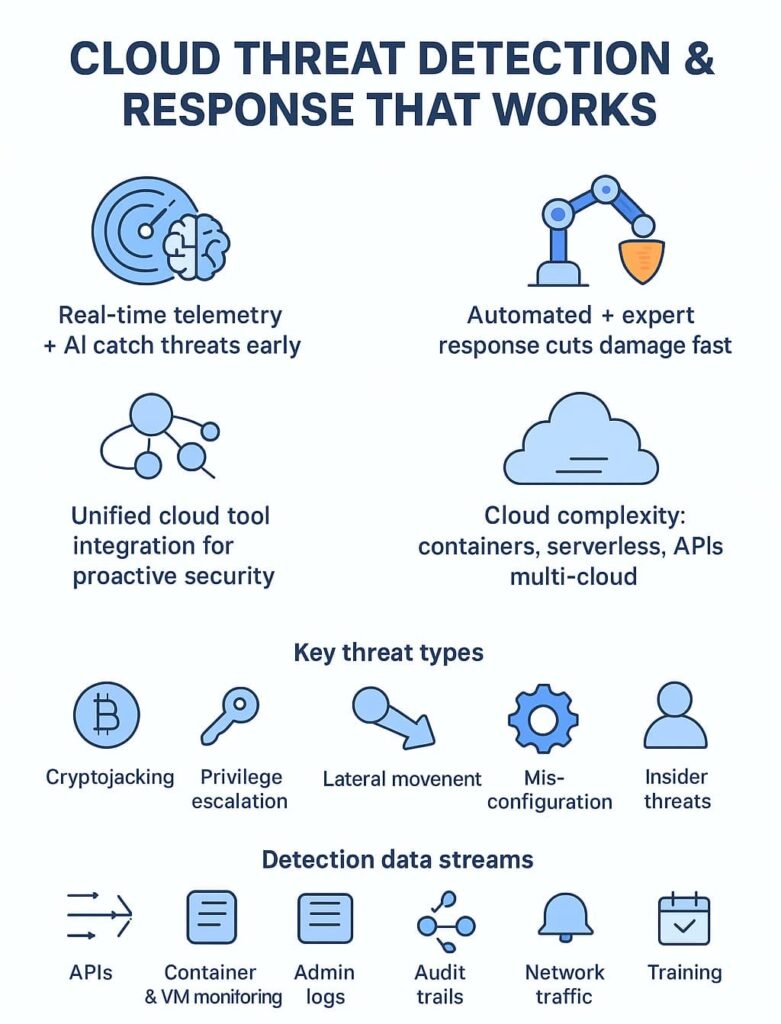
Most cloud setups we audit these days are tangled webs of tech, containers running next to serverless apps, virtual machines talking to dozens of APIs, all spread across different cloud providers. Each piece adds another spot hackers can target.
Bad actors aren’t dumb. They’ve gotten scary good at moving sideways through systems, grabbing admin rights, and hijacking cloud resources to mine crypto. Our incident response team dealt with three cases just last month.
Here’s the kicker: breach costs keep climbing. Recent data shows companies hemorrhaging millions when clouds get compromised. Old-school security tools just can’t handle it, they’re built for networks that barely change. We see this issue constantly during product audits.
The problem? These tools miss half the action. Cloud workloads pop up and vanish in minutes, access rights shift constantly, and most traditional scanners don’t even notice. Security teams end up working in the dark. No wonder our MSSP partners keep asking for better ways to spot threats with cloud security monitoring that adapts in real time.
Credit: SANS cloud security
Catching bad actors in the cloud means watching everything. Through years of auditing cloud security products, we’ve found five key data streams that matter most:
Most detection tools we test use two approaches: good old-fashioned threat rules plus some fancy behavior tracking. Last week, one of our partner MSSPs caught a ransomware attempt just because their tool spotted weird API calls at 3 AM.
Another flagged an admin logging in from Russia when they’re based in Texas. This combo of rules and behavior analysis means fewer blind spots – exactly what our MSSP clients need. [1]
Detecting a threat is only half the battle. Acting swiftly and accurately is what stops attackers in their tracks. Cloud environments demand rapid response due to their dynamic nature.
We rely on two main response types:
The goal is reducing attacker dwell time, the period between initial compromise and detection. The faster the response, the lower the risk of data loss, service disruption, or compliance violations.
A modern CDR solution should deliver:
We’ve learned that falling behind in cloud security can be costly. Here’s a practical approach we’ve taken to strengthen defense:
Using a managed security services provider (MSSP Security) can be a smart move. We bring expertise and round-the-clock monitoring that many organizations struggle to maintain in-house. This partnership frees your team to focus on strategic priorities while we handle threat detection and response.
Cloud environments face unique threats. Here’s how CDR tackles some of the toughest:

Cloud security isn’t without hurdles:
We address these by leveraging automation, AI, and MSSP Security’s expertise to filter alerts, maintain continuous visibility, and coordinate responses efficiently.
AI and automation will increasingly drive cloud security. The fusion of Cloud Detection and Response with Cloud-Native Application Protection Platforms (CNAPP) offers a more proactive and holistic defense. Organizations that embrace these advances can expect faster detection, smarter response, and a stronger security posture against evolving threats.
Cloud threat detection response helps find and stop cyberattacks in real time. It uses cloud security tools like cloud monitoring, cloud anomaly detection, and cloud threat intelligence to spot unusual behavior. By combining these signals, teams can act quickly through cloud incident response to prevent data breaches and limit cloud risk exposure.
Cloud monitoring gives constant insight into workloads, configurations, and network activity. It supports cloud vulnerability management and cloud workload protection by catching early warning signs of attacks.
With cloud event monitoring and cloud audit logs, organizations can track every action, detect suspicious cloud access anomalies, and strengthen overall cloud environment visibility.
Cloud threat intelligence provides context behind alerts and helps predict risks. It connects data from multiple cloud threat correlation sources, enabling faster decisions in cloud incident response.
When integrated with cloud SIEM and cloud security analytics, it builds a clearer picture of active threats across multi-cloud environments and supports smarter response actions.
Preventing a cloud data breach starts with strong cloud identity and access management, cloud encryption monitoring, and cloud security posture management. These tools reduce attack surfaces while cloud intrusion detection and cloud malware detection catch hidden risks.
Regular cloud risk assessment and cloud compliance monitoring keep systems secure and standards up to date.
Cloud threat detection and response is essential for any organization serious about securing its cloud assets. With the right tools, strategies, and trusted partners like MSSP Security, you can stay ahead of attackers, protect sensitive data, and maintain business continuity in an uncertain world.
We offer expert consulting tailored for MSSPs to streamline operations, reduce tool sprawl, and boost service quality. From vendor-neutral product selection and auditing to stack optimization and decision support, our team helps you build a cloud security framework that truly fits your environment.
With 15+ years of experience and 48K+ projects completed, we deliver clear, actionable guidance, from needs analysis and vendor shortlisting to PoC support, ensuring your tech stack aligns with your goals and operational maturity.
Let’s talk and tailor a solution that fits your environment perfectly.