Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Cloud security failures aren’t rocket science, most happen because teams can’t spot problems in time. A new report found 8 out of 10 companies got hacked due to basic oversights in their cloud setup, mainly because they couldn’t track what was going on.
It’s like managing a huge office building without security cameras or guest logs. You’d have no clue who’s coming in, what they’re doing, or if something’s missing until it’s too late.
Want to stop operating blindfolded? Stick around for real steps to securing cloud infrastructure visibility.

Every week, security teams reach out to us about their cloud visibility headaches. The story’s usually the same, they migrated to cloud for better efficiency but lost track of what’s actually running in their environment.
Missing these crucial details puts organizations at serious risk. We’ve audited over 300 cloud environments this year, and the pattern is clear: when teams can’t monitor their setup properly, problems pile up fast.
Shadow IT creeps in, wrong permissions get set, and compliance starts to slip. Many incidents start from detecting cloud misconfigurations too late or missing cloud alerts that flag early signs of exposure.
The numbers paint a grim picture. Most cloud breaches (roughly 65-70%) happened because someone left a storage bucket wide open or gave out too many access rights. Our analysis shows these issues often hide for months before causing problems.
Security teams need real visibility to catch these issues early. In our consulting work with MSSPs, we’ve learned that proper monitoring isn’t just nice to have, it’s the backbone of any decent cloud security strategy. Try defending what you can’t see, you’ll fail every time. [1]
Credit: Simplilearn
Building a complete asset list sounds basic, but it’s where most cloud security plans fall apart. After reviewing hundreds of MSSP setups, we’ve noticed even experienced teams miss about 30% of their cloud resources during manual checks.
Start with these field-tested steps:
We’ve seen top MSSPs run discovery scans weekly, some even daily. The cloud moves quick, your asset tracking needs to keep up. One client found 50 unknown storage buckets after switching from monthly to weekly scans.
Remember: You can’t protect what you don’t know about. A solid inventory isn’t exciting, but it’s the foundation everything else builds on.
Once the assets are cataloged, continuous cloud security monitoring becomes critical. Cloud-native tools such as log collectors and security posture managers help track user activities, system changes, network flows, and more.
But we’ve found that integrating these with a centralized Security Information and Event Management (SIEM) platform provides a deeper, more actionable view.
Actionable tips:
Monitoring isn’t just about spotting attacks, it’s about understanding your environment’s normal behavior.
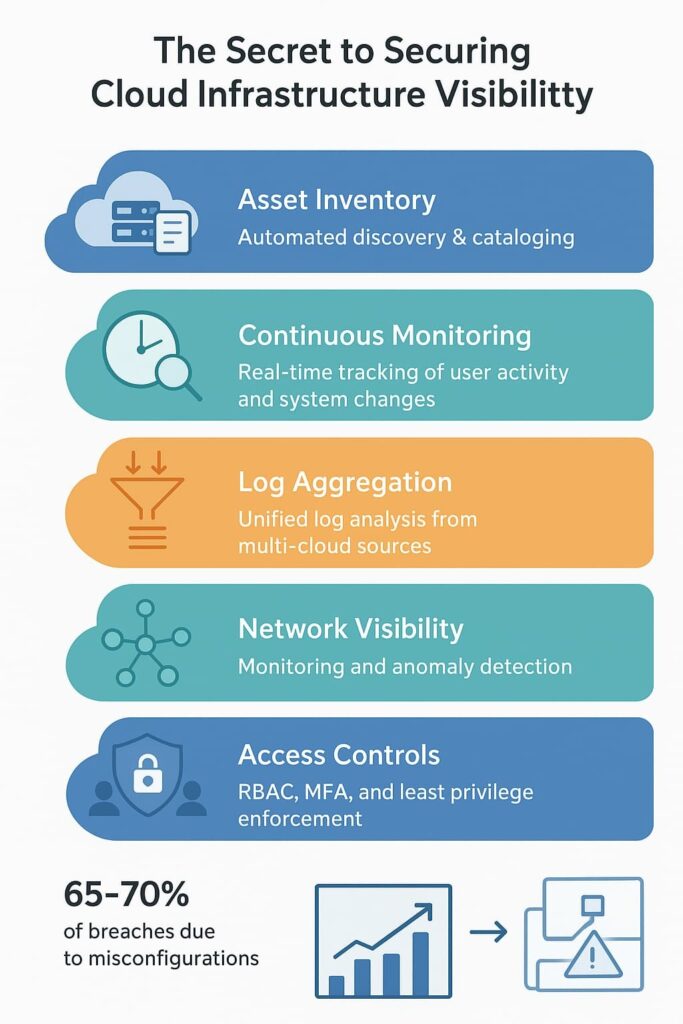
Logs are the breadcrumbs that lead us to security incidents or compliance issues. But cloud environments generate logs from multiple services and regions, often in diverse formats. Centralizing these logs into one platform makes correlation and forensic analysis possible.
What we do:
This consolidation accelerates threat detection and streamlines investigation processes.
Cloud network topologies can be complex and ever-changing. Gaining visibility into subnets, security groups, and network flows helps detect lateral movement by attackers or misconfigured network access.
Best practices include:
Robust network visibility allows you to see not just where traffic flows but if it’s authorized.
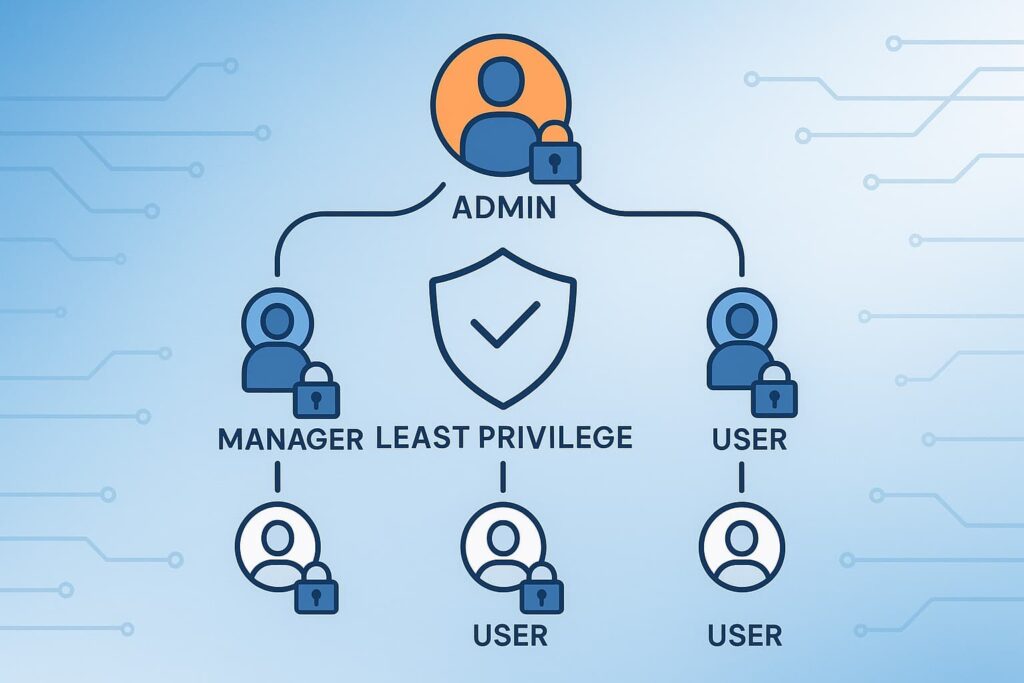
Access control is the first line of defense. We always start here because even the best monitoring tools don’t prevent breaches if attackers gain privileged access.
Key steps:
Applying the principle of least privilege dramatically reduces your attack surface.
Limiting the blast radius of any breach is vital. Network segmentation and microsegmentation isolate workloads so that if one component is compromised, the attacker’s lateral movement is restricted.
Here’s how:
This containment strategy is a proven way to reduce risk and simplify incident response. [2]
| Aspect | Action |
| Asset Inventory | Automate discovery and cataloging of all cloud resources. |
| Continuous Monitoring | Deploy real-time monitoring for user activities and system changes. |
| Log Aggregation | Centralize logs from diverse cloud services for analysis. |
| Network Visibility | Map and monitor cloud network topology to detect anomalies. |
| Access Controls | Implement RBAC, MFA, and least privilege policies. |
| Network Segmentation | Isolate workloads to limit attack surfaces. |
A mid-sized company once suffered a costly data breach due to a misconfigured storage bucket that was publicly accessible. The root cause? Lack of visibility into their storage configurations and permissions across multi-cloud platforms.
After adopting AWS security monitoring and enhanced Azure and GCP security analytics, they reduced exposure dramatically and improved overall visibility.
By implementing automated configuration monitoring, continuous alerts, and strict access policies, they reduced the risk of future breaches significantly. This experience reinforced our belief that visibility combined with automation is key to proactive cloud security.
Securing cloud infrastructure visibility means clearly seeing how your systems, apps, and data behave in the cloud. It involves using tools for cloud security monitoring, cloud asset inventory, and cloud network monitoring to spot unusual activity.
This level of visibility helps organizations reduce cloud infrastructure risks and maintain strong cloud security posture across all environments.
Cloud security monitoring helps businesses track user behavior, detect threats early, and ensure smooth operations. With real-time cloud monitoring, cloud anomaly detection, and cloud threat detection, you can find weak points before they become problems.
It’s a key part of protecting your data, meeting cloud compliance regulations, and maintaining healthy cloud infrastructure security.
Cloud compliance monitoring checks if your cloud setup follows security rules and standards. It works with cloud configuration management and cloud audit trails to track changes and ensure consistency.
By using cloud compliance auditing and cloud security reporting, you gain stronger cloud operational visibility and can respond quickly when something doesn’t meet policy requirements.
Organizations use cloud SIEM integration, cloud security dashboards, and cloud log aggregation to centralize data from different sources.
Combined with cloud workload protection and cloud identity management, these tools improve overall cloud resource visibility. They make it easier to detect issues, automate responses, and strengthen your cloud security architecture.
Securing cloud infrastructure visibility is more than a technical step, it’s a strategic necessity. It enables early threat detection, faster response, compliance, and cost optimization. Native tools alone often fall short; integration and automation strengthen protection.
For teams seeking better security without extra burden, partnering with an MSSP security provider offers expert guidance. With 15+ years of experience and 48K+ projects, we help streamline tools, improve visibility, and enhance performance.
As cloud environments evolve, so must your strategies, continuous improvement and collaboration keep your visibility strong, ensuring your business stays secure, compliant, and in control.