Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Look, nobody plans to leave their cloud doors unlocked. But here’s the raw truth, last year, about 60% of companies got hit because someone screwed up their settings. We’re talking basic stuff: admin passwords left visible, data buckets open to anyone with an internet connection.
Each mess-up cost companies nearly $5 million to fix. Yeah, AWS and Azure have their safety nets, but they won’t catch every dumb mistake.
Want the real scoop on spotting detecting cloud misconfigurations alerts ? Stick around.

Those nagging little setup mistakes in cloud environments, wrong permissions, unprotected storage, encryption turned off, they’re the digital equivalent of leaving windows unlocked in a high-rise. Working with MSSPs, we’ve pulled the numbers: a mind-numbing 90% of cloud breaches start right here.
The cloud setup game has rules. Amazon, Microsoft, Google, they handle the heavy lifting on infrastructure security. But anything running in their cloud? That’s on us, the customers. During our security audits, we see this responsibility gap trip up even seasoned teams.
Most folks don’t realize how fast these seemingly small slip-ups snowball. Last month, an enterprise client faced $800K in fines from a single misconfigured storage bucket. Whether you’re running a Fortune 500 or a startup, cloud settings need constant eyes, the threats don’t sleep, and neither should security checks. [1]
Credit: Fugue, Inc.
Nobody likes getting blindsided by security gaps. That’s why our MSSP partners run non-stop scans against hardcore standards like CIS, NIST, and HIPAA.
Picture a security camera that never blinks, watching encryption settings, access rules, and network configs around the clock. These ongoing evaluations form the foundation of cloud security monitoring, ensuring visibility into every layer of your cloud environment. Last quarter, these checks caught 47 critical misconfigurations before they turned into incidents.
Last quarter, these checks caught 47 critical misconfigurations before they turned into incidents.
Cloud settings change faster than weather in New England. Through direct hooks into AWS, Azure, and GCP, security teams spot trouble the moment it pops up. This live monitoring approach mirrors cloud workload protection practices, where threats and exposure points are tracked continuously across multi-cloud systems.
No more weekly reports gathering dust, our partner MSSPs plug straight into cloud platform APIs for live data feeds.
Just last week, this setup helped catch a client’s dev team accidentally exposing test data within 3 minutes of the change.
Catch problems early, that’s what we drill into every MSSP team. Most of our partners now scan their Terraform files and Kubernetes configs before anything hits production. Working with dev teams, we’ve seen this cut security fixes by 60% in deployment phase.
Simple stuff: plug these scans into build pipelines, let developers fix issues while the code’s still fresh in their heads.
Look, catching bad configs in live systems isn’t enough anymore. Our top-performing MSSPs map out exactly how attackers could chain these misconfigurations together.
Last month, this approach helped a partner spot three linked storage buckets that could’ve given hackers access to their client’s payment data. Sure beats playing whack-a-mole with individual alerts.
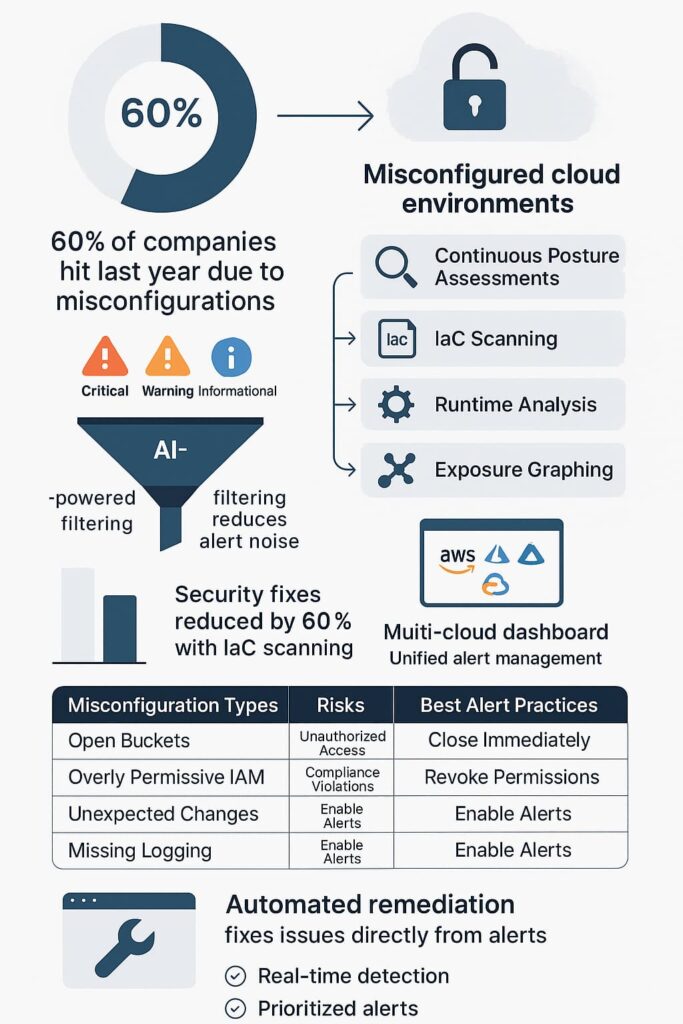
We integrate cloud-native tools like AWS CloudWatch or Azure Monitor to catch issues as they happen. Real-time alerting shortens the detection-to-remediation cycle, crucial in today’s fast-moving threat landscape.
Not all alerts are equal. We classify them as Critical, Warning, or Informational to focus on what matters most. Using AI-powered filtering reduces alert fatigue, ensuring teams aren’t drowning in noise but can zero in on real threats.
For organizations juggling AWS, Azure, and GCP, consolidating alerts into a unified dashboard is essential. It streamlines investigations and response coordination across clouds.
Alert configurations aren’t “set and forget.” We regularly review detection rules and response readiness to adapt to evolving risks and avoid stale or irrelevant alerts.
Some platforms allow us to automate fixes, like closing an open port or revoking excessive permissions, directly from alerts. This cuts down human error and speeds up mitigation. [2]

Early detection of cloud misconfigurations through alerts is your first line of defense against breaches. Without them, risky settings can linger unnoticed, inviting attackers in. For teams handling multi-cloud environments like AWS, Azure, or GCP, monitoring AWS, Azure, and GCP security becomes essential to maintain consistent posture and alert accuracy.
We’ve seen how timely alerts prevented incidents that would’ve exposed sensitive customer data or caused compliance headaches. Moreover, consistent alerting helps demonstrate compliance with regulations like GDPR, HIPAA, and PCI DSS, avoiding penalties.
By proactively identifying faults, alerts help build a stronger security posture, turning cloud security from a reactive firefight into a manageable, continuous process.
| Misconfiguration Type | Risk | Alerting Best Practice |
| Open Storage Buckets | Data exposure, unauthorized access | Real-time monitoring, automated alerts for public access |
| Overly Permissive IAM Roles | Privilege escalation, lateral movement | Regular IAM reviews, least privilege enforcement, alerts |
| Unauthorized Access Attempts | Potential compromise, data theft | Monitor failed logins, suspicious activity, unusual access |
| Compliance Violations | Fines, legal action, reputational damage | Automated compliance checks, alerts for non-compliance |
| Unexpected Changes | System instability, malicious activity | Change management controls, unauthorized modification alerts |
| Missing Logging | Investigation difficulty, compliance issues | Ensure logging enabled, monitor for disabled logging |
Cloud misconfiguration detection alerts usually happen when cloud access controls, permissions, or policies aren’t set right. Weak cloud governance, skipped cloud security audits, and missing automated remediation tools all add up.
Real-time cloud monitoring and strong cloud configuration management reduce these errors and keep your cloud security posture healthy and compliant.
CSPM tools act like constant guardians of your cloud environment. They scan for cloud configuration drift, analyze cloud risk management gaps, and enforce cloud policy compliance.
By using cloud security automation, they catch risky setups before they turn into cloud security breaches. This keeps organizations compliant and reduces costly cloud exposure incidents.
Cloud compliance monitoring ensures your system meets cloud security standards and legal rules. Without it, unnoticed misconfigurations can break compliance or expose data.
By using cloud compliance and risk checks, cloud security audit tools, and cloud security governance, teams stay ahead of audits while maintaining continuous visibility into their overall cloud security posture.
Automated remediation instantly fixes issues that cloud security alerts flag. For instance, if cloud permissions auditing finds overly broad roles, automated cloud security systems can revoke them.
This combination of cloud threat detection, cloud policy enforcement, and cloud security incident management reduces response time and limits potential damage from risky configurations.
Cloud misconfiguration alerts are only as effective as the system supporting them. Pairing continuous posture monitoring with intelligent, risk-based alerting and automated workflows ensures real protection.
MSSP Security combines deep expertise with advanced detection and remediation technology to help organizations stay ahead of misconfigurations without overwhelming teams. For those managing multi-cloud complexity or rapid scaling, expert support makes all the difference.
Partner with MSSP Security to streamline operations, reduce tool sprawl, and strengthen your cloud defenses. Detecting cloud misconfigurations alerts remains essential to safeguarding assets, ensuring compliance, and maintaining visibility across your entire cloud environment.