Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Digital break-ins happen every day, and most companies just can’t catch them all. Some businesses hire a full security team, but that’s expensive. Others cross their fingers and hope nothing bad happens.
A smarter fix? Getting cloud security experts to monitor your system. These tech-savvy folks spot weird login attempts, data leaks, and other sketchy stuff before it becomes a real problem.
Need to know if this makes sense for your setup? Keep reading, we’ll break down the real costs and benefits.
Cloud security monitoring feels overwhelming when you first look at it. Picture dozens of screens filled with alerts, logs, and weird traffic patterns, that’s what security pros deal with daily. We’ve seen companies struggle to make sense of these signals without expert help. That’s where managed monitoring steps in.
The concept works like this: skilled security teams watch cloud systems 24/7, catching odd behavior before it turns ugly. These folks track everything, from who’s logging in to which apps are talking to each other, a foundation built on strong cloud security monitoring principles. Their job? Stop hackers, prevent data leaks, and keep services running smooth.
Through years of helping security providers pick the right tools, we’ve learned that automated alerts aren’t enough. Real humans need to analyze these threats.
Our team has caught attackers who slipped past automated defenses, proving that skilled eyes make all the difference. Whether it’s spotting a hacked account or finding a cloud storage mistake that could leak data, continuous monitoring by actual experts pays off.
Credit: Cloud Security Podcast
Moving to the cloud saves money, sure, but it opens up a whole new set of security headaches. Just last month, our team caught three different attacks that slipped right past standard security tools. Hackers don’t play fair anymore, they’re crafty, patient, and really good at finding weak spots in cloud setups.
Here’s what proper monitoring actually fixes:
Having guided countless providers through tool selection, one thing’s clear, monitoring isn’t optional anymore. The providers who thrive are those who stay ahead of threats while keeping their operations lean. [1]
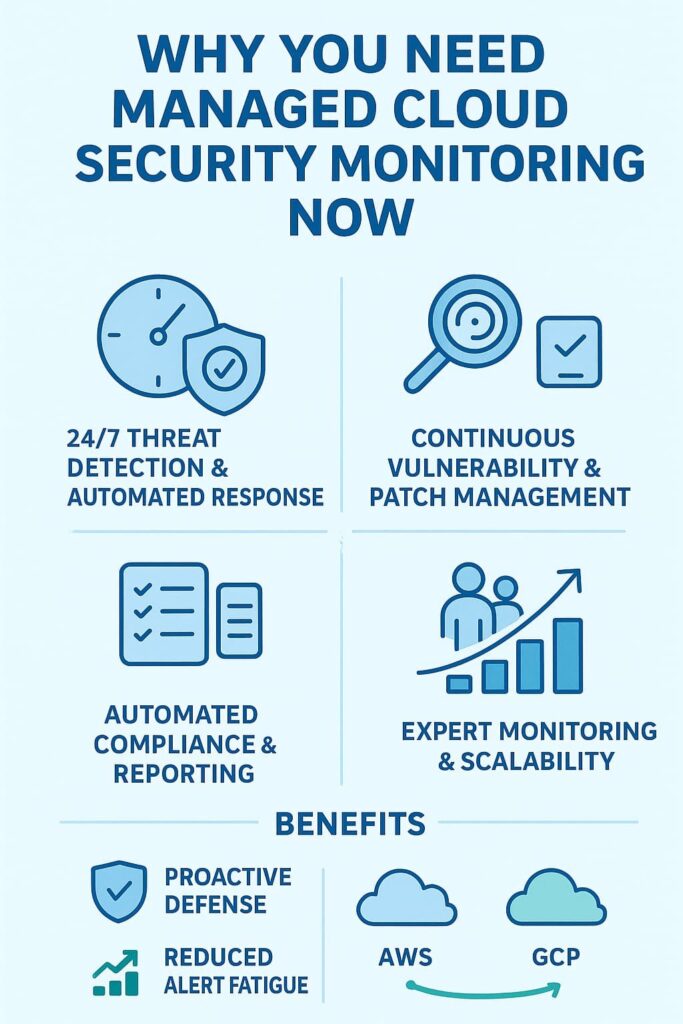
Around the clock, managed cloud security monitoring keeps watch on your cloud workloads, network flows, user behaviors, and API calls. Tools like SIEM (Security Information and Event Management) and XDR (Extended Detection and Response) aggregate data from multiple sources, applying behavioral analytics and anomaly detection to spot threats fast.
When a threat emerges, automated incident response kicks in, isolating compromised resources, revoking risky credentials, or triggering alerts to your security operations center (SOC). This rapid response minimizes damage and helps maintain business continuity.
Cloud environments evolve fast, and so do vulnerabilities. Continuous scanning of your cloud infrastructure, including containers, virtual machines, and infrastructure as code (IaC), helps identify weak points.
To strengthen security posture, many organizations also explore the benefits of outsourced cloud security posture, ensuring consistent protection and faster remediation.
We prioritize remediation efforts based on the exploitability and impact of vulnerabilities, integrating with Cloud-Native Application Protection Platforms (CNAPPs) and Application Security Posture Management (ASPM) strategies to close gaps promptly.
Automated compliance checks keep your cloud configurations aligned with industry regulations. Cloud Security Posture Management (CSPM) tools flag policy deviations before they become compliance violations. Regular audits and detailed compliance reports provide transparency for stakeholders and auditors alike.
Once an incident is detected, managed providers coordinate both automated and manual remediation efforts. This can mean isolating affected systems, rolling out security patches, or launching forensic investigations, all designed to reduce disruption and secure your environment.
Centralized cloud security dashboards deliver a unified view of security events, system health, and compliance status. These insights empower decision-makers to continually refine security posture and prioritize risks effectively.
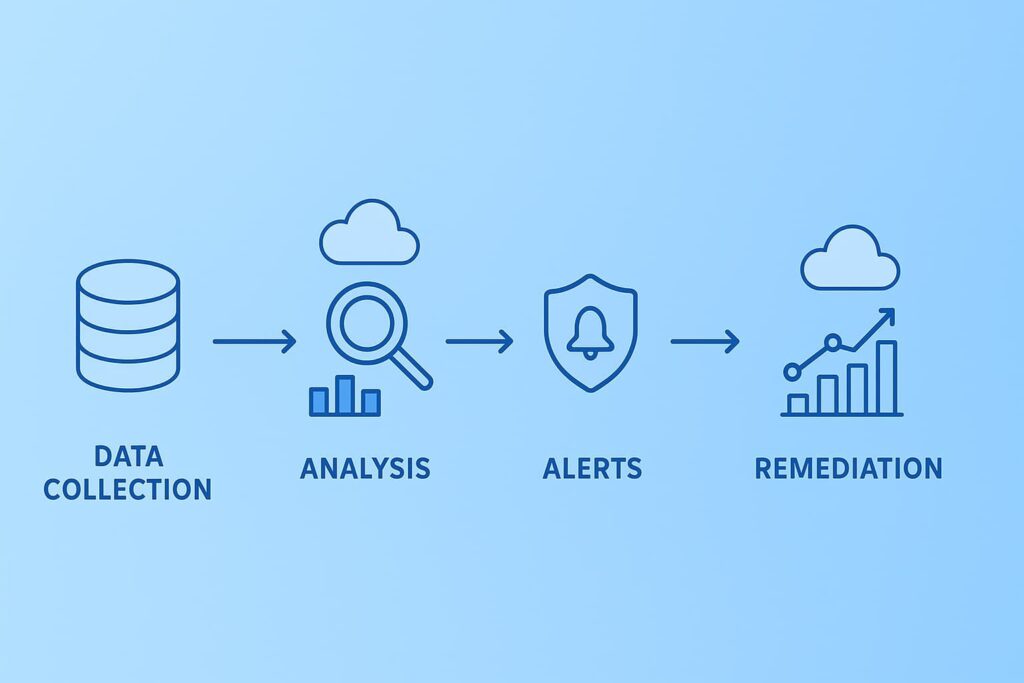
Cloud security monitoring tools collect logs, network traffic data, user activity, and application telemetry from various cloud sources. Consolidating this data into a single platform enables comprehensive analysis.
Advanced analytics and machine learning algorithms sift through massive amounts of data to detect anomalies, such as unusual user behavior, suspicious API calls, or configuration drifts. These systems compare current activity against established baselines to identify potential threats.
Security teams receive immediate notifications through dashboards, email, or messaging platforms. These alerts are prioritized by severity to ensure rapid attention to critical issues without overwhelming analysts.
Automated auditing tools continuously verify that cloud resources conform to established policies and regulatory requirements, helping maintain compliance and prepare for audits.
When risks are identified, managed services swiftly initiate remediation actions, isolating compromised assets, applying patches, or adjusting access controls to prevent escalation.
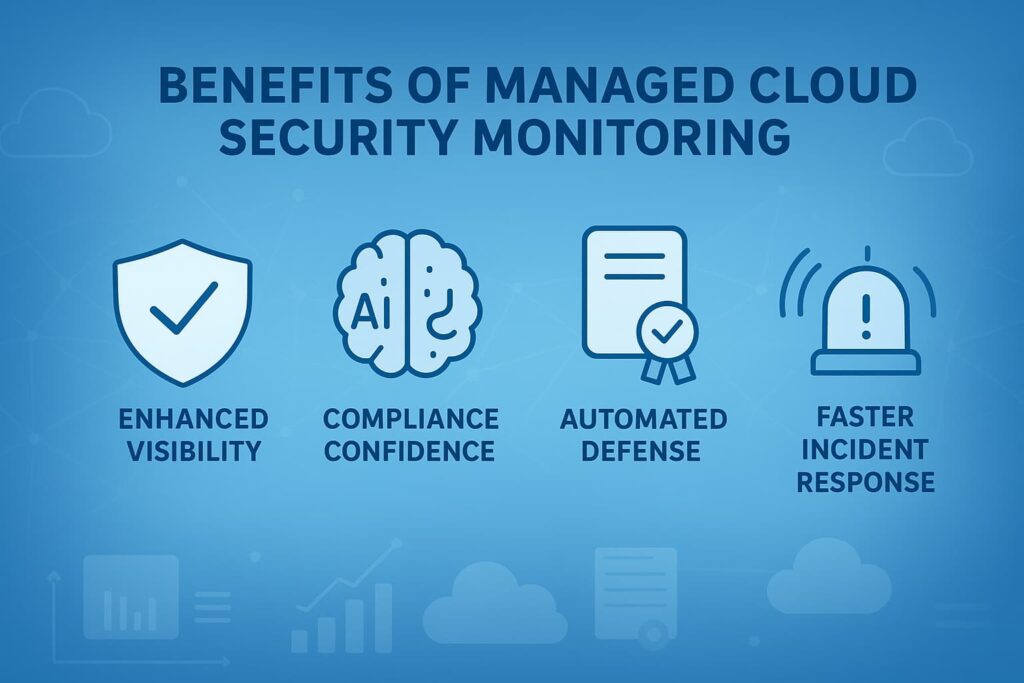
Our experience shows that continuous monitoring paired with rapid automated response drastically reduces the window attackers have to exploit vulnerabilities. Proactive defense is simply the most effective security strategy. [2]
Managing cloud security in-house demands specialized skills and constant vigilance. By partnering with an MSSP Security provider, organizations gain access to expert knowledge and scalable solutions that grow with their cloud environments.
Outsourcing cloud security monitoring frees internal teams to concentrate on strategic initiatives rather than firefighting security incidents. It’s a practical approach that balances security with business agility.
Automated compliance monitoring and reporting reduce the risk of regulatory penalties. Our managed services ensure your cloud environment consistently meets industry standards, easing audit preparation.
Effective cloud security compliance monitoring also ensures that organizations stay audit-ready while maintaining continuous protection.
When selecting a partner for managed cloud security monitoring, consider the following:
Managed cloud security monitoring combines cloud threat detection, cloud compliance monitoring, and automated incident response to help organizations stay ahead of cyber risks. It offers real-time cloud alerts, cloud vulnerability scanning, and cloud access control to protect workloads while maintaining visibility across cloud environments.
Cloud security monitoring tools integrate cloud data aggregation, SIEM integration, and user behavior analytics to identify anomalies early. With anomaly detection, cloud IDS/IPS, and cloud forensic analysis, these tools detect suspicious activity, enabling faster cloud security remediation and reducing the impact of breaches or insider threats.
Automation enhances cloud security posture management and cloud event correlation by enabling real-time analysis and response. Through cloud security automation and cloud orchestration, systems can trigger automated incident response and cloud policy violation detection, ensuring quicker mitigation without waiting for manual intervention.
Cloud compliance monitoring ensures alignment with standards using cloud audit trails, cloud audit readiness, and cloud security compliance reports.
It verifies that cloud configuration management, encryption monitoring, and cloud governance meet required baselines, helping organizations maintain accountability while simplifying audit preparation and reporting.
In our work, the blend of technology, process, and human expertise defines successful cloud security. Managed Cloud Security Monitoring isn’t a one-size-fits-all solution, it’s an adaptable, proactive approach that evolves with your cloud footprint and threat landscape.
By partnering with an experienced MSSP Security team, you gain continuous protection, compliance confidence, and operational efficiency. It’s a smart investment that empowers organizations to harness the full power of the cloud, without compromising security.
Partner with MSSP Security to Strengthen Your Cloud Protection