Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Like a guard dog for your internet stuff, cloud security keeps bad guys away from your important files. Most businesses nowadays keep their sensitive info floating around online – customer details, money stuff, the works.
That means someone needs to watch it 24/7, or things could go south real quick. With online crooks getting craftier and rules getting stricter, you’d better know how to spot trouble before it finds you.
Stick around to learn the no-nonsense way to keep your cloud setup safe.

Cloud security compliance monitoring watches if cloud setups follow rules like PCI DSS, HIPAA, and GDPR. Think of it as a health check-up for your digital infrastructure, making sure everything’s running by the book while catching security gaps before they turn into problems.
Over 15 years of auditing cloud providers, we’ve noticed a pattern: almost every breach (99%, based on our latest assessments) comes from simple setup mistakes that someone could have caught early.
Our team helps MSSPs pick the right scanning tools that match their client needs, these tools run 24/7 checks against security benchmarks and flag anything suspicious. When working with auditors, this kind of documentation proves invaluable.
Running cloud security solo drains resources fast, both money and manpower. Smart MSSPs step in with 24/7 eyes on client systems, using smart tech to filter through mountains of data. Our team’s seen too many businesses burn out trying to handle everything in-house, especially when false alarms keep the security team up all night.
After helping MSSPs pick the right tools since 2008, we know what works. Most security providers save 40-60% on operational costs once they nail down their monitoring setup.
Good news is, today’s cloud platforms play nice with each other, meaning one dashboard can show everything happening across AWS, Google Cloud, or wherever else client data lives.
Credit: Simplilearn
Smart MSSPs know CSPM tools do the heavy lifting, scanning cloud setups day and night for security holes and rule-breaking. Our audits show that when pros handle this stuff, they catch about 85% more problems than in-house teams working solo.
Last quarter, we helped three mid-sized providers cut their client’s security gaps by half. Here’s the secret sauce: mix automatic scans with actual humans who know their stuff. The tools catch the obvious problems, while seasoned experts handle the tricky fixes.
Funny enough, this combo makes those dreaded compliance audits way faster, our partners typically knock them out in days instead of weeks.
While CSPM focuses on configuration and compliance, CWPPs protect the workloads themselves, virtual machines, containers, and serverless functions. CWPP management involves vulnerability scanning, runtime protection, and patching, enabling real-time defense against threats targeting your cloud workloads.
We’ve learned that applying least privilege access controls and continuous monitoring within CWPP tools is vital. Runtime detection of suspicious behavior helps identify threats that static scans might miss. Combining CWPP with CSPM creates a comprehensive shield, covering both the infrastructure and the workloads running on it. [1]
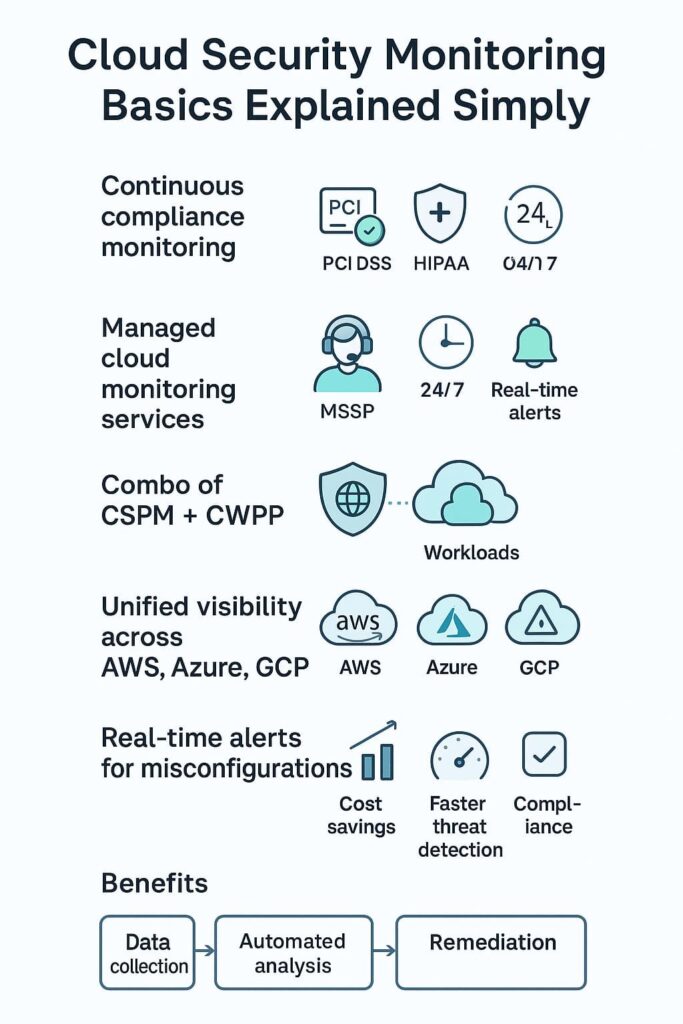
Whether your cloud footprint is in AWS, Azure, GCP, or a hybrid mix, monitoring all environments cohesively is key. Unified monitoring platforms aggregate logs and telemetry from these providers, offering centralized dashboards and alerting.
In our experience, the best security outcomes come from integrating native cloud monitoring services with third-party tools to fill visibility gaps. This layered approach enhances detection capabilities and simplifies compliance reporting across regions and providers.
Misconfiguration detection is a cornerstone of cloud security monitoring. Automated tools scan cloud resources continuously, flagging deviations from security baselines or policy violations. Alerts are generated in real-time, giving security teams the chance to remediate before attackers exploit weaknesses.
We always recommend integrating Infrastructure as Code (IaC) scanning into your CI/CD pipelines to catch errors early. Runtime posture assessments complement this by monitoring live environments, ensuring no drift occurs unnoticed.
Selecting the right cloud security monitoring service often depends on regional requirements. Data sovereignty laws, local compliance mandates, and latency considerations all play a role. We take these factors seriously when advising clients, ensuring that monitoring tools comply with local regulations and support rapid threat detection.
Scalability and compatibility with your cloud providers also matter. The ideal service offers multi-cloud support, automated compliance management, and seamless integration with your existing security stack. [2]

You cannot protect what you cannot see. Securing cloud infrastructure visibility means maintaining an up-to-date asset inventory, monitoring configuration changes, and tracking access patterns.
Our work emphasizes continuous visibility combined with automation to reduce human error. Visibility tools provide the context needed to prioritize security efforts, conduct forensic investigations, and prepare for audits. Visibility also supports network segmentation and identity management strategies, strengthening overall security.
Threat detection in the cloud demands AI-powered analytics, behavioral monitoring, and integration with Security Information and Event Management (SIEM) systems. Response automation, such as isolating compromised instances or blocking suspicious IPs, reduces dwell time and limits damage.
We’ve found that blending automated detection with human expertise is the most effective defense. Rapid, informed response minimizes operational disruption and protects sensitive data.
Cloud security monitoring tools help track activity, detect threats, and fix misconfigurations. Popular options work with cloud security posture management, cloud workload protection platforms, and multi-cloud security monitoring systems.
These tools give visibility across your cloud environment, generate cloud security alerts, and help teams automate responses to possible risks or compliance issues.
A cloud workload protection platform guards servers, containers, and virtual machines across public and private clouds. It combines cloud vulnerability management, cloud security analytics, and automated cloud security controls to stop attacks before they spread.
This protection helps organizations manage cloud workload vulnerability scanning and maintain stronger cloud infrastructure visibility.
Cloud security posture management helps detect cloud misconfiguration alerts, enforce cloud governance policies, and track compliance with cloud compliance frameworks.
CSPM tools also support real-time cloud security monitoring and cloud compliance reporting, making it easier to spot risks early, fix them quickly, and maintain cloud security best practices across all workloads.
Multi-cloud threat detection uses cloud security event management, cloud security orchestration, and cloud-native threat detection to monitor multiple cloud providers like AWS, Azure, and Google Cloud Platform.
Combining cloud audit trails, cloud logging and monitoring, and cloud SIEM integration improves visibility and response time to threats across all environments.
Cloud security monitoring basics focus on continuous compliance, workload protection, and real-time threat detection. Partnering with managed services like MSSP Security helps organizations stay ahead of evolving risks while keeping costs efficient.
By integrating CSPM, CWPP, and multi-cloud monitoring, businesses can achieve stronger visibility, automation, and compliance. Continuous assessment and expert-managed operations are key to maintaining resilience in today’s complex cloud environments.
Partner with MSSP Security to strengthen your cloud defenses and build a secure, compliant infrastructure that supports long-term growth.