Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

System logs hit IT teams like a tsunami – constant alerts, endless error messages, and those midnight pings nobody wants. It’s a mess that eats up hours of work time. A log management service sorts through this chaos, spots the stuff that matters, and handles those annoying compliance reports.
Your folks can finally quit playing detective with server logs at 2 AM and do their actual jobs. Sound good? Stick around to see how managed log management service works.
Every IT system tells its story through logs. But parsing these digital chronicles gets messy fast. We’ve seen seasoned teams struggle as their monitoring dashboards fill up with endless streams of data.
Data floods in faster than anyone can handle – server logs, app errors, cloud metrics, and network alerts pile up by the second. Back in 2021, our team spent 30+ hours weekly just organizing logs from different sources. Manual tracking just doesn’t cut it anymore.
Today’s tech stack doesn’t help either. Hybrid environments spread across three clouds, containers that spin up and die in minutes, microservices talking to each other – it’s a tangled web that needs rock-solid log tracking.
Bad actors know where to hit where it hurts – those blind spots in logging that nobody caught. Meanwhile, auditors want perfect records for HIPAA, PCI-DSS, and GDPR. We’ve guided MSPs through 200+ compliance audits, and incomplete logs always cause the biggest headaches. That’s where strong log management for compliance frameworks make a real difference, ensuring regulatory alignment and complete visibility across data sources.
Most security teams we work with are stretched thin. They’re juggling daily fires while trying to build expertise in log analysis and SIEM tools. The market’s talent shortage makes it worse – finding and keeping log management specialists burns through budgets fast.
Our journey started the same way. We’d waste days stitching together fragmented logs, missing critical alerts until it was too late. That’s when we knew MSPs needed a better way – a managed approach that actually works. [1]
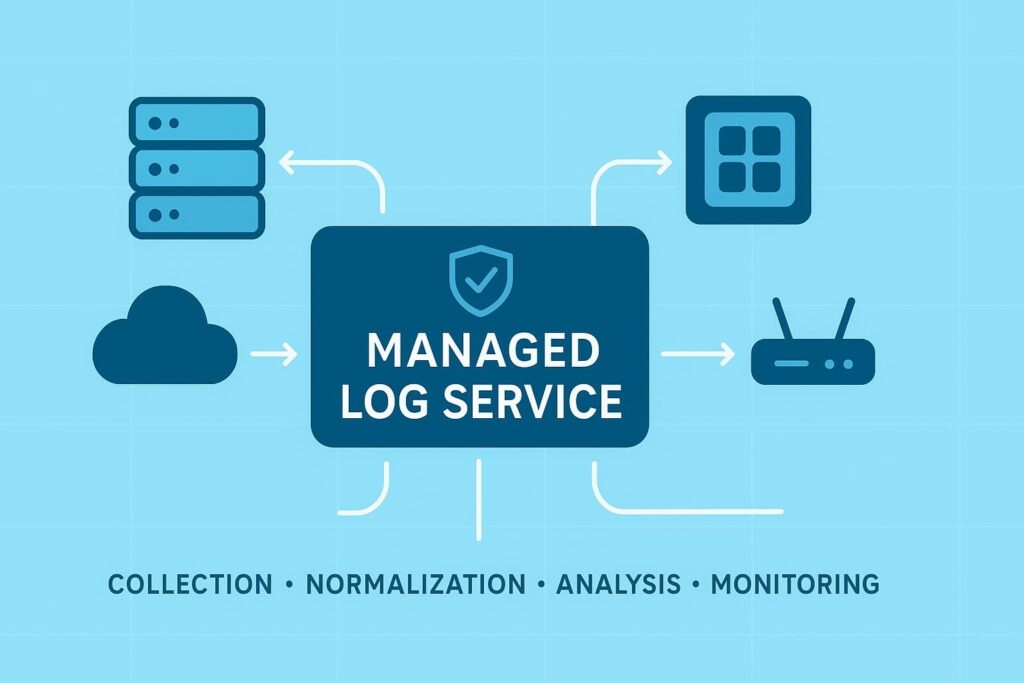
Think of log management as mission control for your digital footprints. We take charge of the whole process – grabbing logs automatically, storing them safely, making sense of the data, and flagging issues before they blow up. Our team’s been doing this for 8+ years, helping MSPs dodge the headache of building their own log systems from scratch.
We don’t just collect logs and call it a day. There’s real expertise behind every alert, report, and compliance check. MSPs partner with us because their teams shouldn’t waste time wrestling with log servers when they could be growing their business.
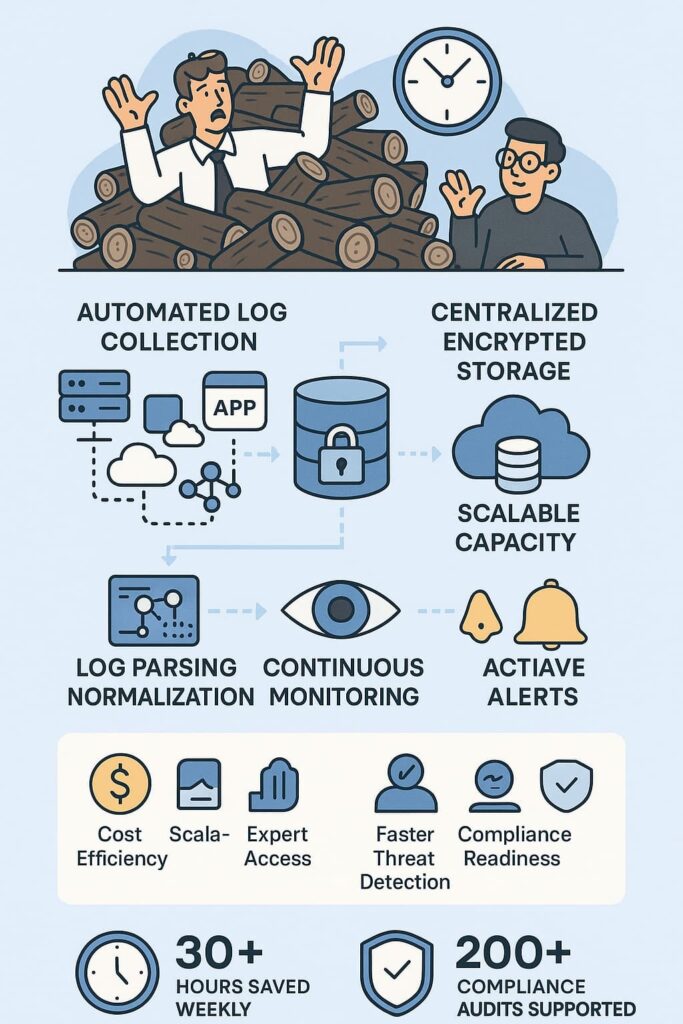
This comprehensive approach means you get continuous, expert oversight of your logs, backed by automation and machine learning for efficiency and precision.
Credit: Christian Lempa
We’ve seen firsthand how managed log management transforms operations:
By partnering with MSSP Security, organizations free internal teams from tedious log tasks and focus instead on strategic initiatives. [2]

While managed log management offers many advantages, it’s important to consider a few factors:
Another key factor is scalability, some companies reduce infrastructure strain through outsourced log collection and retention, allowing them to store and analyze data efficiently while maintaining compliance.
If any of these points resonate, exploring managed log management as a strategic investment makes sense.
A managed log management service helps organizations handle log collection, log aggregation, and log storage solutions from one place. It automates log parsing and normalization across system logs, application logs, and network traffic logs.
With centralized log collection, teams can analyze data faster through real-time log monitoring and reduce manual maintenance using log workflow automation.
Centralized log monitoring platform setups simplify audit log management, security event monitoring, and compliance log retention. They use log data encryption and log data integrity controls to protect sensitive information.
Unified log correlation and log filtering also help detect suspicious user activity logs and threat detection logs, making it easier to create accurate log compliance reporting.
By combining log anomaly detection, log correlation rules, and AI-powered log analysis, managed log management services boost early threat detection. They use machine learning for logs to spot patterns across endpoint logs, hybrid cloud logging, and incident response logs.
Teams can act quickly using log dashboards, alert management, and forensic log investigation to stop security risks fast.
Log retention policies and log retention automation are key parts of compliance and audit preparation. Managed services manage scalable log storage and log archival using cloud-based log storage or hybrid setups.
They ensure compliance log retention, log data backup, and log data governance align with data regulations while maintaining log privacy controls and log user access control.
Handling logs in-house can quickly become a resource drain and a security risk. By leveraging a managed log management service like MSSP Security, businesses gain robust, scalable visibility backed by expert analysis and compliance assurance.
We’ve helped organizations overcome the challenges of log aggregation, parsing, real-time monitoring, SIEM integration, and incident response, freeing their teams to focus on innovation and growth while we manage the logs that secure their operations.
If you’re ready to simplify log management and strengthen your security posture, partner with MSSP Security today.