Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Server logs are a mess. Period. IT folks spend way too much time digging through mountains of data spread across different dashboards, logins, and tools. Sure, your cloud servers keep logs. So do your apps, databases, and that dusty storage server nobody talks about.
Getting these scattered pieces under one roof isn’t just about making life easier – it’s about catching the bad stuff before it hits the fan. Stick around to see how putting your logs in one place can save your team’s sanity and centralized log management solution.
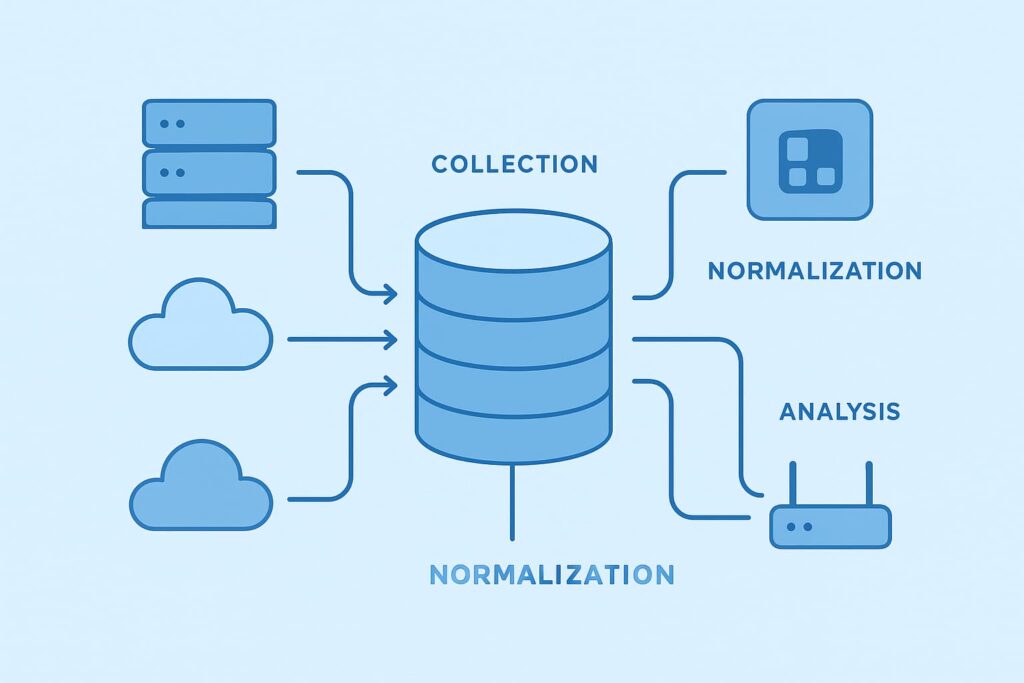
Nobody wants to dig through scattered logs – trust us, we’ve spent years helping security providers untangle that mess. CLM pulls together the flood of data from your servers, apps, networks, and cloud stuff into one searchable hub. Think of it as mission control for your entire system’s paper trail.
Most security teams start with logs spread across different places, each speaking its own language. Some store stuff locally, others push to the cloud, and there’s always that one legacy system doing its own thing. Been there. When incidents pop up, techs waste hours bouncing between screens instead of fixing problems.
Our consulting work with MSSPs shows that bringing logs under one roof changes everything. Teams catch issues faster, reports write themselves, and compliance audits become less of a headache.
The right CLM setup handles everything from grabbing those logs to making sense of them, even firing off alerts when something looks fishy. No more crossed wires or missed signals – just clear visibility across the board.
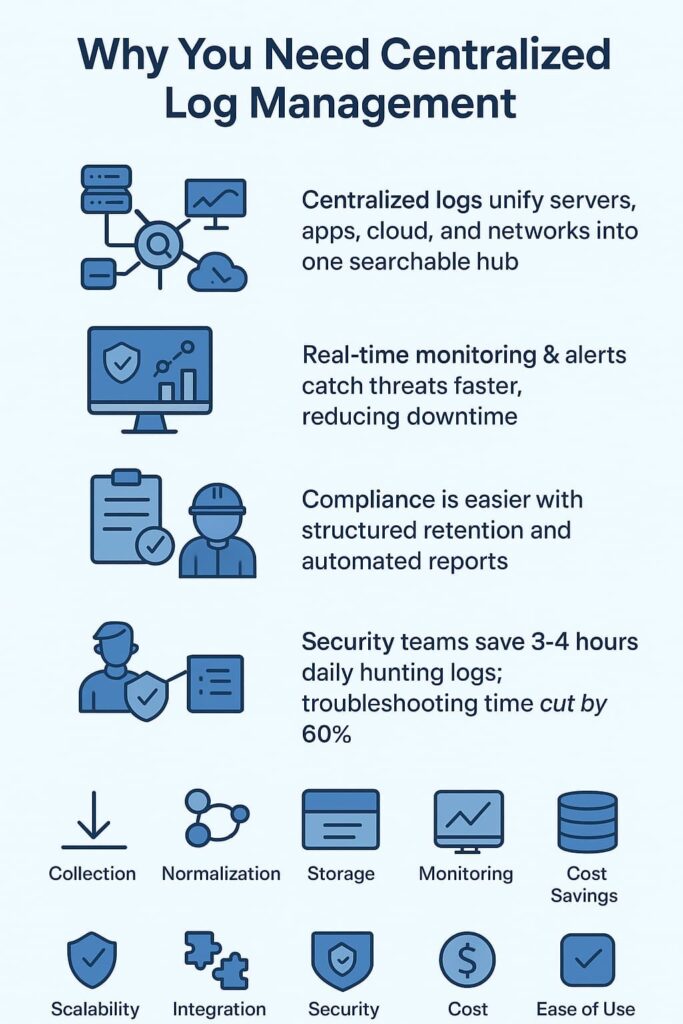
Let’s cut to the chase – scattered logs are killing productivity. Our security partners tell us the same story: their teams waste 3-4 hours daily just hunting down log data across different systems. Meanwhile, attackers slip through the cracks, hiding their tracks in the flood of unconnected logs. And when auditors come knocking? That’s another nightmare altogether.
Here’s what proper log management does for security teams:
Our team has spent years in the trenches with MSSPs, watching them transform from reactive firefighters to proactive threat hunters. The secret sauce? Getting those logs working together under one roof. [1]
Credit: CodeLucky
Logs originate from everywhere: servers, firewalls, applications, cloud platforms, endpoints, you name it. Centralized solutions gather this data via agents deployed on hosts or agentless protocols like syslog, SNMP, and APIs. The key is multi-source log collection that doesn’t miss critical events.
Raw logs vary wildly in format. Normalization transforms them into a standard structure so you can analyze data uniformly. Enrichment adds context, timestamps, user IDs, geolocations, threat intelligence, making logs more meaningful for investigations.
Centralized log repositories balance hot storage for real-time querying and cold storage for compliance archiving. Efficient log indexing strategies enable lightning-fast searches across millions of log entries, saving time during incident response.
Continuous log scanning detects anomalies, security incidents, and infrastructure issues. Customized alerts notify the right teams instantly, empowering swift action before problems escalate.
Dashboards, query languages, and reports turn raw data into actionable intelligence. Visualizations reveal trends, anomalies, and patterns that inform security strategies and operational improvements.
We’ve observed how correlating logs from endpoints, network devices, and applications exposes sophisticated attack patterns. Centralized log correlation rules and anomaly detection are invaluable for uncovering stealthy intrusions and ransomware activity.
The log management for compliance approach also reinforces audit readiness and data protection, ensuring each log event aligns with regulatory standards. Centralized log correlation rules and anomaly detection are invaluable for uncovering stealthy intrusions and ransomware activity.
Automated alerting and integration with security incident detection platforms keep defenders a step ahead.
When system performance dips, pinpointing the root cause fast is crucial. With a centralized log repository, you quickly search across system logs, application logs, and network logs simultaneously. This reduces mean time to resolution and keeps your teams focused on strategic work instead of firefighting.
Compliance audits demand a reliable audit trail of log data, complete, searchable, and retained per policy. Centralized log management enforces log retention policies and supports immutable logs and log encryption to protect data integrity. Automated log report generation streamlines audit preparation.
We’ve helped clients reduce storage costs by filtering out redundant logs and employing log compression. Scalable log storage architectures, including cloud-native logging options, enable flexible growth without breaking the budget.
Normalization standards and log parsing pipelines ensure log data is consistently structured, enabling precise log analytics. This consistency is critical for effective forensic log analysis and security investigations.
Making the right selection depends on several key criteria:
From our experience in MSSP security, solutions that enable flexible log data export and multi-source collection provide the most operational agility. For organizations seeking scalability and expert oversight, a managed log management service can centralize control while reducing internal workload.
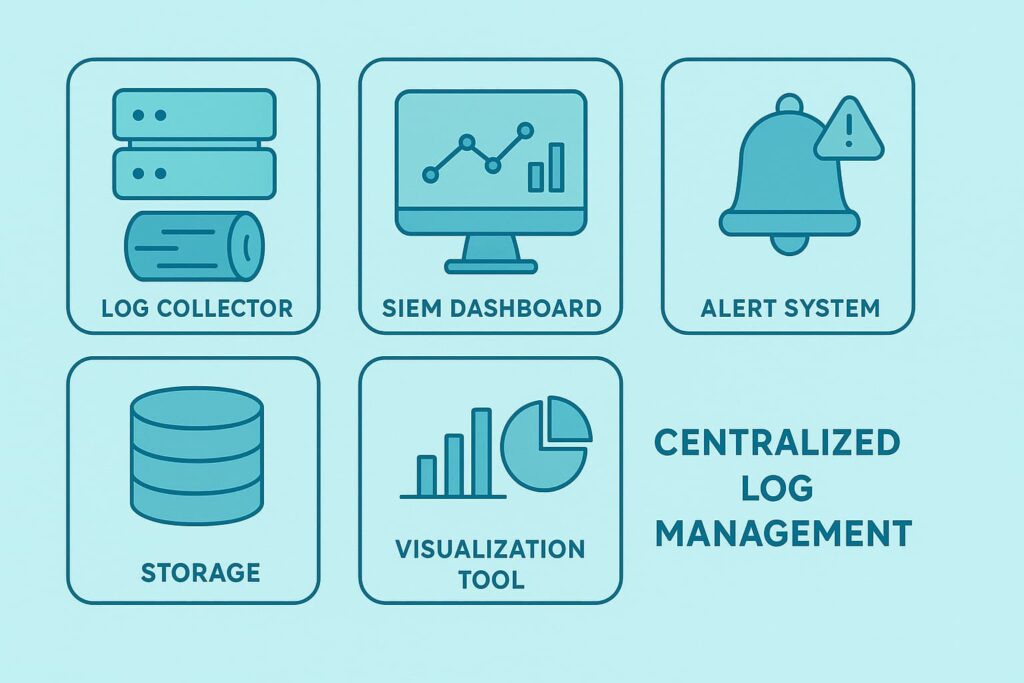
A centralized log management solution brings together system logs, application logs, and network logs into one centralized log repository. It helps simplify log collection, log aggregation, and log normalization across cloud and on-prem environments.
With centralized logging architecture, teams can easily run log search, improve log visibility, and maintain compliance log retention.
Centralized log management improves security by enabling real-time log monitoring and log alerting across all sources. Security teams can use log correlation, log analytics, and forensic log analysis to detect unusual activities and prevent threats early.
This process supports log anomaly detection, log encryption, and log access control to ensure log data integrity.
Log normalization and log enrichment standardize and add context to raw data collected from multi-source log collection. These steps make log parsing, log correlation rules, and automated log analysis more accurate.
A clean log processing pipeline allows analysts to identify patterns faster, supporting threat hunting logs and efficient security incident detection.
A centralized log management platform helps with audit trail management, logging compliance, and compliance audits. It keeps immutable logs for transparency and supports log retention policies, log compression, and scalable log storage.
Teams can also create log report generation and log verification processes that meet compliance log retention and log policy enforcement standards.
Centralized log management (CLM) is essential for organizations aiming for stronger security and operational efficiency. By unifying diverse log data, CLM enables proactive defense, faster troubleshooting, and audit-ready compliance.
Many MSSPs see it as the foundation of a resilient IT environment, enhancing visibility, reducing overhead, and improving incident response. With over 15 years of experience and 48K+ projects, we help MSSPs streamline operations, optimize tools, and boost service quality through expert consulting, vendor selection, and stack integration.
Join us to build your centralized log management strategy and strengthen your IT operations.