Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

When auditors show up, logs are your best friend – simple as that. It’s like having a security camera for your systems, catching everything from failed logins to weird file changes. Healthcare folks and retailers know this pain – HIPAA and PCI rules don’t mess around.
Look, wrestling with log files isn’t anyone’s idea of fun. But here’s the deal: dump those scattered logs in one place, and suddenly you’ve got a clear picture. Plus, having experts watch your back beats losing sleep over missed alerts.
Want the real scoop on making logs less of a nightmare? Read on.
Managing logs separately creates chaos – ask any security team drowning in alerts from different tools. We’ve seen this headache countless times while helping MSSPs evaluate their tech stack. When logs live in different places, finding that one crucial alert becomes like searching for a needle in multiple haystacks.
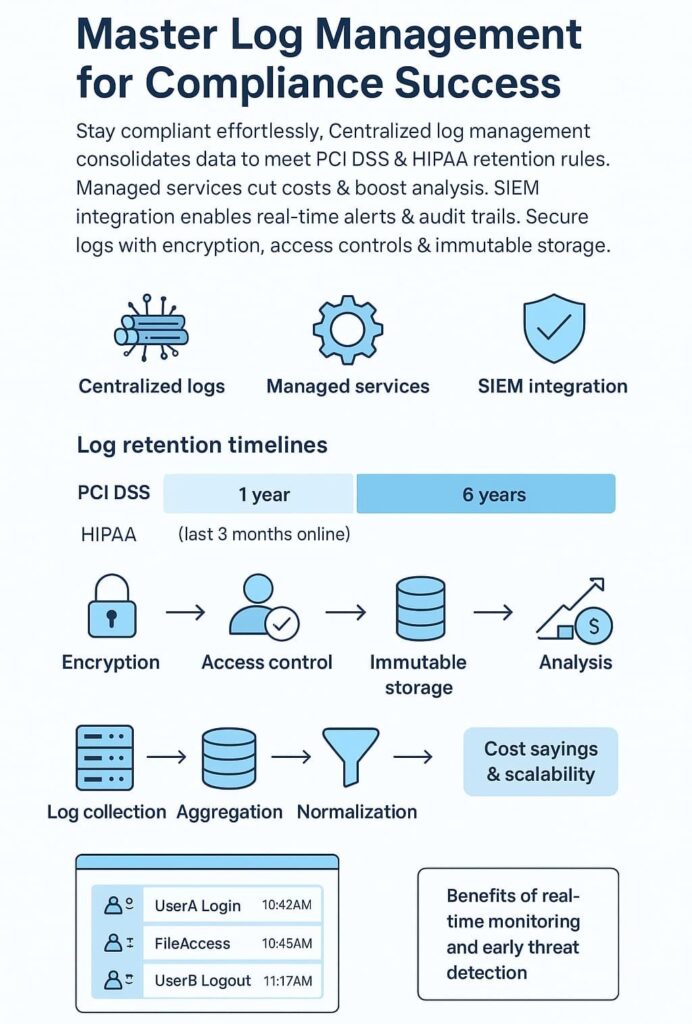
Organizations need their logs in one spot, period. Having worked with dozens of security providers, we know that unified logging isn’t just nice-to-have anymore. PCI DSS demands one year of logs with three months ready access. HIPAA pushes it further – six years of records. These aren’t suggestions, they’re requirements with teeth.
The right setup transforms this mess into something useful. Logs flow into a central hub, get cleaned up, indexed, and locked down tight. Our audits consistently show that MSSPs struggle without this foundation. Think about it – when an auditor asks for six months of access logs, would you rather search one system or twenty?
Let’s face reality – most security teams drown in logs. After reviewing hundreds of MSSP setups, we’ve seen how raw log volume crushes in-house teams. That’s where managed services shine. No more buying endless storage or hunting for log experts who cost a fortune.
Smart providers handle the heavy lifting. Our assessments show they typically save MSSPs 40-60% compared to DIY approaches. The good ones automatically scale when log volumes spike (like during incidents) and adapt their retention as rules change. No scrambling to add storage or tweaking backup jobs.
These specialists turn messy logs into useful intel. Through years of product evaluations, we’ve watched them spot threats that basic tools miss. They’ll enrich logs with threat data, flag weird patterns, and speed up investigations. When auditors or incidents hit, that expertise proves priceless.
Compliance is about more than just ticking boxes; it’s about maintaining a reliable, auditable record of all relevant activities. PCI DSS requires logs be retained for at least one year, with immediate online access to the last three months. HIPAA, more flexible but stringent, often calls for logs to be stored for six years or as per organizational policy.
Meeting compliance log retention requirements involves:
Adhering to these requirements reduces audit risks and supports swift incident response with reliable log data. [1]
Credit: Anuuj Medirattaa
Logs hold sensitive information about system operations and security events. Secure log storage is non-negotiable for compliance and operational security.
This means logs must be encrypted at rest and in transit, access-controlled, and stored immutably. Immutable log storage prevents unauthorized modification or deletion, preserving data integrity for audit and forensic use.
Advanced log analysis techniques, such as log correlation, event severity classification, and alarm correlation, turn raw data into actionable insights.
Parsing and log normalization standardize diverse log formats, while taggings and indexing enhance searchability and filtering. These capabilities enable proactive log monitoring and alerting services, letting security teams detect threats in real time.
SIEM (Security Information and Event Management) platforms build on log management’s foundation by adding security analytics, real-time event correlation, and automated alerting. While centralized log management handles storage and basic analysis, SIEM solutions enhance threat detection and incident response.
Integrating SIEM with your log management solution allows:
This layered approach fortifies your security posture without sacrificing compliance readiness.
Simply collecting logs is not enough. Finding critical events buried in mountains of data requires intelligent log analysis. Techniques like ML log analytics and AI-driven log anomaly reporting help identify unusual patterns or deviations from baseline behaviors. Event severity classification prioritizes alerts, reducing false positives and focusing attention on real threats.
Effective event log analysis includes:
This empowers security teams to uncover hidden threats and maintain compliance continuously.
Continuous log monitoring is the frontline defense for compliance and security. Managed log monitoring services watch logs in real time, triggering alerts for failed login attempts, unauthorized access, malware detection, or policy violations. Automated alerting reduces manual effort and accelerates incident response.
Log monitoring alerting services provide:
Organizations in cities or regions face unique compliance and infrastructure challenges. Cost-effective log management tailored to local regulations and latency requirements is vital. Managed log services with regional data centers offer scalable solutions that optimize log storage costs without compromising security or compliance.
Benefits include:
Compliance audits demand detailed, unalterable audit trails documenting user actions, system changes, and security events. Audit trail log management ensures every relevant event is recorded with timestamps and user identifiers. This traceability supports investigations, regulatory reporting, and continuous compliance monitoring.
Best practices include:
Log management for compliance means collecting, storing, and analyzing logs to meet legal and security standards. A good log management solution uses centralized log management to track user activity logs, system logs, and access logs. This helps with compliance monitoring, audit trail creation, and proving data integrity during compliance audit logs.
Log retention policies depend on regulations. For example, PCI DSS log retention and HIPAA log retention have specific timelines for keeping audit trails and access control logs. These compliance log retention rules ensure that secure log storage and immutable log storage preserve data integrity while giving teams time to run forensic log analysis if needed.
Companies can use a managed log management service or even outsourced log collection to simplify operations. These services often include log aggregation, log parsing, and SIEM integration for real-time log monitoring.
Log management automation helps with log tagging, event correlation, and log normalization, creating a cost-effective log management setup with strong compliance monitoring.
Centralized log management brings all event log analysis and log correlation into one dashboard. It boosts visibility, supports threat detection logs, and simplifies compliance audit logs.
With cloud log management or hybrid log management, you gain log storage scalability, log backup, and log recovery, key log retention benefits for growing data environments.
Modern compliance thrives on unified log management combining centralized solutions, managed services, and SIEM integration. Encrypting, securing, and analyzing logs proactively ensures data integrity and regulatory alignment with PCI DSS and HIPAA.
Strengthen your compliance posture with a cost-effective, scalable log management solution that enhances visibility and audit readiness. Our experts help MSSPs streamline operations, reduce tool sprawl, and optimize stacks through vendor-neutral consulting, integration support, and actionable recommendations.
With 15+ years of experience and 48K+ projects completed, we’ll help you build a mature, efficient security framework. Explore Managed Log Management Services