Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Anyone running a network knows about IDS/IPS, those finicky security tools that sometimes cause more headaches than they prevent. Yeah, they catch bad guys trying to break in, but they also flood your inbox with alerts about perfectly normal traffic.
Setting these things up right is a pain in the neck, and keeping them running smoothly? That’s a whole other story. Most of us have been there: staring at screens full of alerts at 2 AM, wondering if that spike in traffic is a real attack or just the nightly backup. But get past the initial mess, figure out the sweet spots in tuning, and these systems actually do what they’re supposed to.
Stick around, I’ll show you how to make these tools work without losing your mind..
Picture a busy highway where every car is a packet of data. Network analysis means checking each vehicle, where it’s going, what’s inside, and whether anything looks off. Sometimes it’s obvious, like a sports car suddenly doing 20 mph. Other times it’s subtle, maybe a delivery truck that’s a bit too heavy.
The real work happens in those monitoring tools that dig deep into the data streams. They’re not perfect, sometimes they get twitchy about normal stuff, and you’ve got to retrain them. Like teaching an overprotective guard dog the difference between the mail carrier and an actual threat.
Things to Watch For:
And yeah, it takes time to get it right. The systems need constant adjustments, kind of like maintaining an old car, you can’t just set it and forget it. Sometimes you’ll chase false alarms, other times you’ll catch something serious before it becomes a problem. That’s just how it goes.
Nobody wants to babysit security systems around the clock. That’s the real appeal of managed IDS/IPS services, letting someone else handle the constant stream of alerts and updates. These services put trained security folks behind the wheel, people who spend their days fine-tuning detection rules and sorting through the noise to find real threats.
The difference shows up pretty quick in the numbers. False alarms drop off, detection gets sharper, and your team isn’t burning hours chasing ghost alerts. Plus, these services tap into threat feeds that track new attack patterns (something most in-house teams don’t have time or budget for).
Also, one survey found that 65% of companies regularly use IDS/IPS tools as part of their security stack, which suggests adopting vendor-managed or third-party-assisted IDS/IPS is common enough to benefit from mature offerings. [1]
Key advantages we’ve seen:
Farming out intrusion detection to a Security Operations Center makes sense when you can’t justify a full-time security team. It’s like having a whole squad of experts watching your network without the overhead of hiring them all yourself.
These SOC teams don’t just stare at screens, they’re actively hunting threats and connecting dots that automated systems might miss. Many managed security service providers build on this with MSSP core service offerings that cover continuous monitoring, threat intelligence, and tailored response strategies. When something sketchy pops up, they’ve got response plans ready to go, cutting down the time between detection and fix.
What you typically get:
Think about it, most attacks don’t schedule appointments during business hours. Having pros watching your network while everyone else sleeps isn’t just convenient, it’s becoming necessary.
Credits: CBT Nuggets
Unlike IDS, which only detects threats, a Network Intrusion Prevention System (NIPS) takes action in real-time to block malicious traffic. We find NIPS invaluable for stopping attacks like botnet communications or command-and-control traffic before they reach critical assets.
NIPS typically operates inline, meaning it’s placed directly in the data path, allowing it to drop, redirect, or quarantine suspicious packets instantly. This proactive stance reduces attack surfaces and limits the chance of breach escalation.
Key NIPS capabilities include:
Configuring rules and alerts is where theory meets practice. We often start by customizing rule sets to match the network’s characteristics and threat profile. Overly broad rules can flood analysts with false positives, while too narrow ones risk missing attacks.
Alert prioritization is critical. Setting severity levels helps ensure that only actionable threats generate high-priority notifications. Regular reviews and system tuning are essential because attackers constantly change tactics.
A good configuration strategy includes:
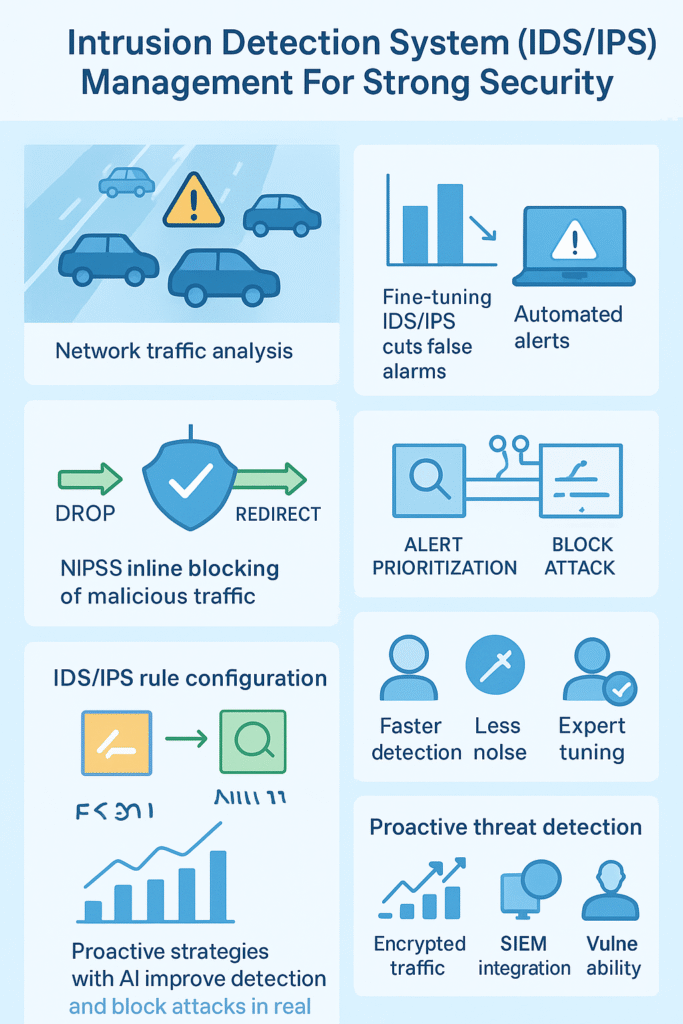
Threats don’t take breaks, so neither should monitoring. We recommend continuous surveillance of network activity using dedicated teams and automated tools. This nonstop approach catches attacks during off-hours when internal staff might be unavailable.
Real-time monitoring involves analyzing logs, packet captures, and event streams with behavioral analytics engines that can flag suspicious activity promptly. Immediate alerting enables rapid incident response, which can mean the difference between a minor scare and a major breach.
Advantages of 24/7 monitoring:
False positives, benign activity flagged as threats, are a major headache. They waste precious time and can cause alert fatigue. We find that reducing false positives is a balancing act requiring careful rule tuning, data enrichment, and smart filtering.
Techniques we use include:
By systematically addressing false positives, security teams can focus on real risks without drowning in noise.
Picking the right managed IDS/IPS provider means evaluating several key factors. We look for vendors offering flexible sensor management, seamless integration with existing tools, and strong threat intelligence capabilities.
Especially now, with ~50% of organizations expected to be using MDR services by 2025, many businesses find that a vendor with deep SOC capabilities helps them detect threats more quickly and reduce costs. [2]
Other factors influencing the choice:
Due diligence here pays off in smoother operations and better security outcomes.
While network-based IDS monitors traffic, Host-Based Intrusion Detection Systems (HIDS) focus on activity within individual devices. We often deploy HIDS on servers and critical workstations to track file integrity, user behavior, and system logs.
HIDS is essential for spotting insider threats or compromised accounts that evade network-level sensors. It also complements network IDS by providing detailed forensic data after an incident.
Important HIDS features:

Proactivity means staying ahead of attackers by hunting for threats rather than just reacting. We advocate continuous monitoring with baseline profiling, so deviations stand out early. Integrating threat intelligence and AI-driven analytics enhances the ability to spot new, unknown attack vectors.
This approach includes:
By adopting proactive strategies, risk mitigation becomes more dynamic and effective.
Network traffic analysis is key to improving IDS configuration because it looks at normal patterns and baseline profiling to separate real threats from harmless activity. Using packet inspection, protocol analysis, and behavioral analytics, administrators can fine-tune rulesets and adaptive filtering.
This reduces false positive alerts, strengthens event correlation, and makes alert prioritization more reliable. Over time, system tuning, change management, and log management help lower noise so that intrusion prevention becomes more accurate.
When IDS and IPS tools are tied into SIEM integration, security operations centers gain better visibility for intrusion prevention and incident response. Security alerts from signature-based detection, anomaly-based detection, and heuristic analysis are enriched with log retention policy data and threat intelligence.
Event correlation and attack signature database updates improve security event notification, while automated response and automated playbooks streamline remediation workflow. This integrated threat prevention approach reduces manual effort and speeds up risk mitigation.
Encrypted traffic handling is a challenge because packet inspection and application-layer inspection are limited without SSL inspection or encrypted payload inspection. IDS configuration and IPS configuration often rely on endpoint protection, firewall integration, and perimetric defense to monitor encrypted session monitoring effectively.
Role-based access and privileged user tracking support compliance auditing, while network segmentation and network topology mapping keep sensitive data secure. Advanced techniques like deep packet inspection and zero-day threat detection add another defense layer.
Vulnerability assessment feeds into adaptive filtering by identifying weak points in the network topology. IDS and IPS systems then use anomaly detection, baseline profiling, and point-in-time analysis to watch for deviations. Combined with malware detection, host-based IDS, network-based IDS, and redundant sensors, this ensures multi-vector protection.
Audit trails, reporting dashboard insights, and continuous improvement efforts all help system tuning and scalability planning. Together, these steps reduce the attack surface and support defense-in-depth strategies.
A managed security service offers remote monitoring, virtualized sensor deployment, and cloud IDS deployment to strengthen IPS evasion prevention. Using threat modeling, penetration testing, and defense-in-depth, providers update attack signature databases and custom rulesets regularly.
They also guide vendor management, reporting retention, and compliance auditing with clear audit trails and reporting dashboard metrics. Continuous improvement, remediation workflow, and proactive defense strategies ensure better risk mitigation, reduced data exfiltration detection issues, and long-term security compliance.
IDS/IPS management goes beyond simply deploying tools. It requires continuous tuning, expert monitoring, and layered defenses that cut false alarms, accelerate detection, and block attacks in real time. When combined with proactive threat hunting, it strengthens resilience against evolving threats. Start by reviewing your current IDS/IPS setup and consider expert-managed monitoring to stay ahead.
Learn how we can help optimize your security stack with tailored insights and hands-on guidance.