Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Outsourced Intrusion Detection Monitoring gives companies a practical way to stay ahead of cyber threats without overwhelming internal teams. With attacks growing in scale and frequency, businesses can’t afford blind spots or delayed responses.
Instead of relying solely on stretched IT staff, outsourcing provides constant surveillance, expert analysis, and immediate alerts when suspicious activity occurs. This approach helps close security gaps, reduces risk, and offers peace of mind knowing professionals are always watching the network.
In a landscape where breaches can cripple operations overnight, organizations need smarter defenses. Keep reading to see why outsourcing may be the safeguard you need.
Let’s face reality – the cyber crime wave isn’t slowing down. The FBI’s numbers paint a pretty grim picture: attacks shot up 300% since 2019, and that’s probably lowballing it.
The bad guys aren’t just going after the big fish anymore – they’re picking off smaller companies left and right, figuring they’re easier to crack. Mom-and-pop shops, local manufacturers, even that dentist office down the street – nobody’s too small to be a target anymore.
Here’s the thing about building your own security team: it’s kind of like trying to start a pro sports franchise from scratch. You need star players (who cost a fortune), top-notch equipment (another fortune), and someone who knows how to run the whole show (yep, another fortune). We’re talking about dropping at least $500,000 just to get the basics going – and that’s before anyone’s even started working.
The talent hunt’s no picnic either. These security pros? They’re like rare Pokémon – everybody wants ’em, but good luck catching one. And if you do manage to snag someone good, some big tech company’s probably gonna wave a better offer in their face six months later.
That’s where these outside security teams come in clutch. They’ve already got everything running – the fancy monitoring tools, the threat databases, the whole nine yards. Plus, they’ve seen pretty much every trick in the book. When some hacker tries something funny at 3 AM, these folks don’t need to Google what to do – they’ve handled it a hundred times before.
Think of it like having a SWAT team on speed dial. Sure beats trying to train your own security force while the bad guys are already at the door. [1]

Think of it like having a whole team of security nerds (the good kind) watching your network day and night. They’ve got their eyes glued to screens showing all sorts of data flowing through your systems. Any weird stuff pops up, they’re on it.
Here’s what’s usually included:
The best part? It works pretty fast. One medium-sized manufacturing company got their monitoring up and running in just 72 hours. Within the first month, their new security team caught and stopped three attempted ransomware attacks that slipped past their regular firewall.
These outside teams use some serious tools advanced setups for an intrusion detection system that cost more than a luxury car, and artificial intelligence that spots patterns faster than any human could. But you don’t have to understand all that technical stuff – that’s their job. Your job is running your business while they handle the digital bad guys.
Most companies find this setup works better than trying to do everything in-house. It’s like having a top-tier security team without having to build one from scratch. The monthly cost usually ends up being less than hiring just one full-time security expert, and you get an entire team watching your back 24/7.

Let’s break down the main advantages of this approach:
| Benefit | What It Means for You |
| 24/7 Continuous Monitoring | No gaps in security coverage, any time of day |
| Cost Savings | Avoids hiring and tooling costs for an internal SOC |
| Access to Expertise | Security pros with the latest skills and tools, plus the added managed IDS IPS service benefits that most companies can’t build in-house. |
| Improved Compliance | Helps meet regulatory demands with ease |
| Faster Incident Response | Quicker detection and containment of threats |
| Focus on Core Business | Your team works on priorities, not alerts |
Expanding on these: continuous monitoring means threats get caught when they happen, not hours later. Cost savings are real, building an internal SOC can cost millions annually. Outsourcing slashes that figure. Access to expertise means you benefit from analysts who specialize in threat detection and response, backed by advanced tech you might not afford on your own.
Compliance is a big headache for many businesses, and this service helps stay on the right side of regulations by generating detailed reports and maintaining security policies. Faster incident response means less downtime and damage. And of course, your internal IT staff can devote time to projects that grow the business rather than firefighting security alerts.

Here’s what the service actually does day to day:
From our perspective, the combination of these tasks creates a safety net that’s hard to build alone. It’s like having a full-time, expert security team watching over your digital assets without the overhead of training and managing them yourself. [2]
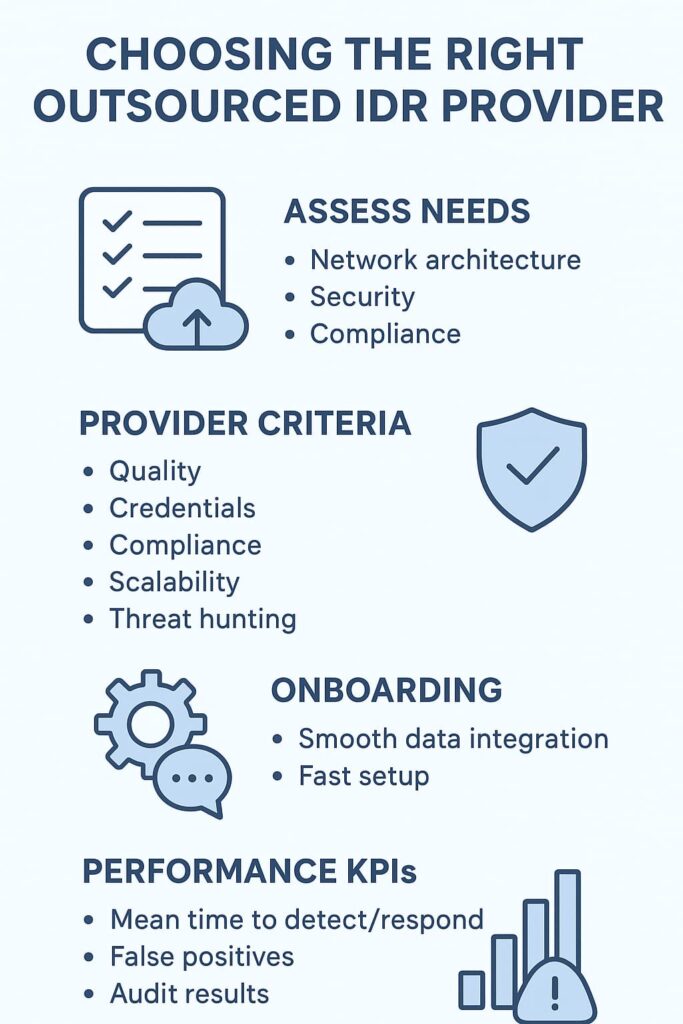
Picking your provider isn’t just about price. It’s about finding a partner who fits your needs. Start by assessing your network architecture, security requirements, and compliance obligations. Do you need hybrid cloud monitoring? What regulations apply to you?
Next, evaluate providers based on:
Onboarding is critical. Integration of your data feeds with their monitoring platforms should be smooth and fast. We’ve seen delays here cause frustration, so clear communication upfront is key.
Finally, track performance using KPIs like mean time to detect and respond, false positive rates, and compliance audit results. These indicators help ensure you get real value and security improvements.
To get the most out of outsourced monitoring, consider these steps:
We remember a client who initially struggled with slow response times. After refining SLAs and communication protocols, their security posture improved dramatically. It’s a process, and staying engaged pays off.
Outsourced intrusion detection means a third party runs the tools and monitors threats, while managed intrusion detection often includes more strategic oversight. Intrusion detection monitoring services add continuous threat monitoring and real-time intrusion detection.
The choice depends on whether a business wants daily operations handled externally or prefers to keep more control in-house.
Network intrusion detection scans traffic for unusual activity, while cybersecurity monitoring adds wider coverage across systems. Together, they support intrusion detection and response by spotting ransomware detection, insider threat detection, or malware detection early.
Using IDR services, organizations gain real-time intrusion detection, incident response, and continuous threat monitoring for stronger cyber resilience.
Managed security services offer monitoring and alerts, but SOC as a service and outsourced SOC deliver full-time coverage. These teams handle intrusion detection and response, vulnerability monitoring, and cyber threat monitoring around the clock.
Security operations center outsourcing helps businesses overcome SOC staffing challenges while giving access to threat intelligence, automated threat detection, and advanced threat detection.
An intrusion detection platform often pairs with SIEM monitoring to connect data across systems. Behavioral analysis highlights insider threat detection, network anomaly detection, or malware behavior analysis.
Combined with SIEM integration, network sensors, and endpoint monitoring, this approach strengthens cyber defense monitoring. It enables faster incident response, forensic analysis, and automated threat response while supporting a clear security audit trail.
Getting pros to watch your network is like having a top-notch security team without the hassle of building one from scratch. They’re on guard while you sleep, catching the weird stuff before it becomes a nightmare.
Sure beats trying to do it all in-house, especially when skilled security experts are harder to find than a needle in a digital haystack. For most companies facing constant cyber threats, it’s the smartest way to stay protected without breaking the bank.
👉 Join MSSP Security today and get expert support tailored to your needs.