Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
California businesses probably spend way too much time overthinking their firewall management choices. The harsh truth? Most companies here need more than just some fancy security box sitting in a server room.
They’re looking at complex networks spread across multiple offices (sometimes spanning 500+ miles from San Diego to Sacramento), each one facing its own set of cyber threats. A decent managed firewall provider doesn’t just sell equipment, they’re practically an extension of the IT team, watching networks 24/7 and jumping on problems before they blow up into major headaches.
For anyone trying to figure out this whole security mess in California, here’s what actually matters.
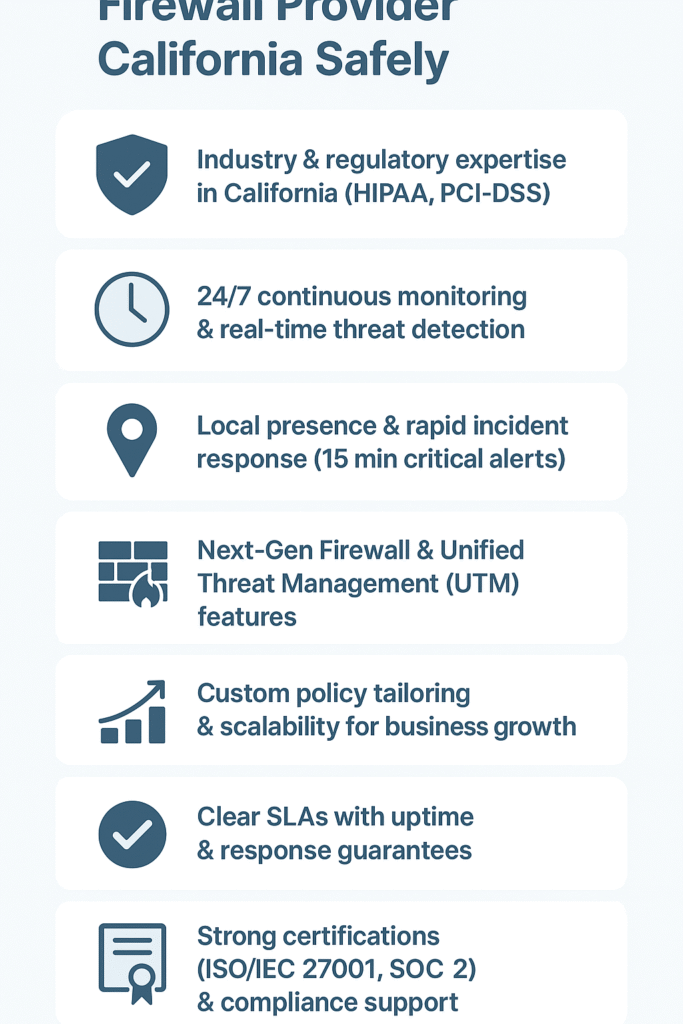
The best firewall providers in California seem to get one thing right—they know their industries inside and out. Through years of working with local businesses, they’ve picked up on best practices from managed firewall services that ensure continuous protection and tailored policy enforcement:
Picking someone who’s dealt with similar California companies means fewer growing pains down the road.
Let’s face it, HIPAA and PCI-DSS are complex and critical. In 2024, California residents aged 60 and over suffered the most losses from cybercrimes, with over $800 million reported. [1] A provider needs to show they’ve actually handled these regulations before, not just read about them. Signs of solid regulatory experience include:
Nobody wants a provider figuring things out as they go along. The right certifications prove they’ve done their homework, but they shouldn’t just be collecting badges. Their team needs to show how these standards shape their daily work.
These fancy acronyms matter because they force providers to follow strict security rules. Good providers don’t just frame their certs, they build them into everything from how they handle patches to responding when something looks suspicious.
Having boots on the ground in California makes a real difference. A provider with local teams (especially in tech hubs like SF, LA, and San Diego) usually gets things done faster. They understand state privacy laws and can show up when needed, not just connect through some remote session.
When something breaks, waiting around isn’t an option. The best providers commit to specific response times like:
Strong ties with the big names in firewalls mean better support when things get tough. The managed firewall services market was valued at $3.62 billion in 2024 and is projected to reach $9.84 billion by 2033, exhibiting a CAGR of 11.71% from 2026. [2] Look for providers who work closely with at least two of these:
Modern firewalls do way more than just block bad traffic, they spot weird behavior, control which apps can run, and stop threats before they cause damage. A provider needs to know how to use these features properly, not just turn them on and hope for the best.
Credits: Simplilearn
You’d think IPS would be standard by now, but some providers still treat it like an optional add-on. A decent IPS catches the nasty stuff before it hits your network, kind of like having a bouncer who actually knows what they’re doing. Most California companies we’ve worked with say it’s saved their bacon more than once, especially with all these new attacks popping up.
Unified Threat Management (UTM) bundles everything together, which makes sense when you’re trying to keep track of what’s happening on your network, especially when integrated with proactive threat hunting to identify unusual patterns before they escalate.
Nobody wants those one-size-fits-all security policies that some providers try to push. Each business needs its own ruleset, what works for a 50-person law firm in San Francisco probably won’t cut it for a 500-person manufacturing plant in Ontario. Good providers take time to figure out:
Growth shouldn’t break your security setup. If adding 20 new employees means waiting three weeks for firewall changes, something’s wrong. The right provider grows with you and incorporates managed vulnerability management to continuously assess and mitigate potential risks, whether that means:
Let’s be real, cyber attacks don’t wait for business hours. Having someone watching the network at 3 AM on a Sunday might seem like overkill until that one time you really need it. The monitoring team should know your network well enough to spot weird behavior right away.
Numbers tell stories if you know how to read them. Good providers show you what’s actually happening on your network without drowning you in useless alerts. They’ll point out stuff like:
Talking to a different person every time you call is exhausting. Your support team should know your setup without having to look it up every time. They should remember that your CEO needs special access for their trading app, or that your dev team runs tests at weird hours.
When something breaks, you need to know exactly who to call and what happens next. No provider’s perfect, but the good ones tell you upfront:
The “deny everything unless allowed” approach isn’t just security-speak, it’s common sense. Most network breaches we’ve seen happened because someone left too many doors open. Sure, users might complain about strict access rules, but that beats explaining to the board why customer data got leaked. A solid provider won’t cave to pressure to loosen things up “just this once.”
Firewall rules get messy fast. One client had over 2,000 rules, half of them outdated. Good providers clean house regularly by:
Think of network segments like fire doors in a building, they contain problems when things go wrong. Most California businesses need at least 3-4 separate zones:
Putting firewalls in the right spots matters more than most people think. We’ve seen companies with fancy next-gen firewalls at their internet edge but nothing between their sales and accounting networks. That’s like having a steel front door but leaving all the interior doors wide open.
Nothing’s worse than a firewall that doesn’t play nice with the rest of your network. A provider needs to know how to:
Remote work changed everything. Now providers need to handle:
Raw logs don’t help much, you need someone who can turn network data into useful info. Good providers show you stuff like:
Nobody likes dealing with auditors, but decent reporting makes it less painful. Your provider should give you:
And they shouldn’t need two weeks’ notice to pull basic reports together.
Money talks, especially in California’s managed security market. Small providers come and go, but you need someone who’ll be around next year. Look for companies that:
Any provider can talk big during sales pitches. What matters is what their clients say when you actually call them. Good signs include:
AI’s not magic, but it helps spot things humans miss. The best providers use it to:
Just don’t trust anyone who claims their AI catches everything.
Nobody wants to stay late patching firewalls. Your provider should handle updates without breaking things. That means:
Get everything in writing. Good SLAs spell out:
Watch out for providers with SLAs full of loopholes and exceptions.
Reports shouldn’t just sit in your inbox. Useful reporting includes:
Certifications cost money and time, providers who maintain them show they’re serious. But check if they’re actually following the rules, not just hanging certificates on walls.
Someone in Nebraska might charge less, but they won’t understand why CalOPPA matters to your business. Local providers get that California’s different. They know:
Plus, they can show up when things really go wrong.
When comparing a managed firewall provider California businesses trust, focus on practical details like firewall monitoring California, firewall rule management California, and firewall technical support California. Ask about managed firewall cost California, firewall SLA California, and firewall service provider reviews California.
Look at options for Fortinet managed firewall California, Cisco firewall management California, and Palo Alto firewall provider CA so you can match features with your network size and needs.
Many small businesses overlook firewall compliance California requirements until they face fines or audits. Choosing a HIPAA firewall provider California or PCI-DSS firewall services CA is important if you handle medical or credit card data.
Managed firewall security California can include firewall compliance audits CA, firewall reporting California, and firewall policy management California to help pass inspections and reduce risk.
Before you sign a managed firewall service agreement CA, read carefully about firewall incident response CA, firewall device replacement CA, and firewall patch management CA timelines. Make sure 24/7 firewall monitoring California and real-time threat detection firewall CA are included.
Ask about firewall automation CA, firewall log management California, and firewall scalability California to be sure your system grows with your business.
A local firewall provider California can set up VPN firewall services California, site-to-site VPN CA, or IPSEC managed firewall CA for secure remote access. This setup, paired with firewall network segmentation CA and firewall access control California, helps protect sensitive data.
Managed network security California teams can also assist with firewall configuration CA, firewall cloud integration California, and endpoint firewall protection CA for remote staff.
Even with next-generation firewall CA and unified threat management CA, firewall penetration testing CA helps find weak spots before attackers do. A strong provider of California firewall services will combine firewall risk management California, firewall breach prevention CA, and firewall threat intelligence CA.
They may offer firewall consulting CA, firewall policy design CA, and firewall training California so you understand how to keep your system strong.
Choosing a managed firewall provider in California means balancing technical features, regulatory compliance, and local responsiveness. The right provider offers industry expertise, real-time threat management, customizable policies, scalable services, and 24/7 monitoring, along with solid incident response and clear SLAs. Protecting sensitive data and staying ahead of threats isn’t optional, it’s essential.
For expert guidance in selecting the right tools and optimizing your tech stack, join our MSSP consulting services today.