Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

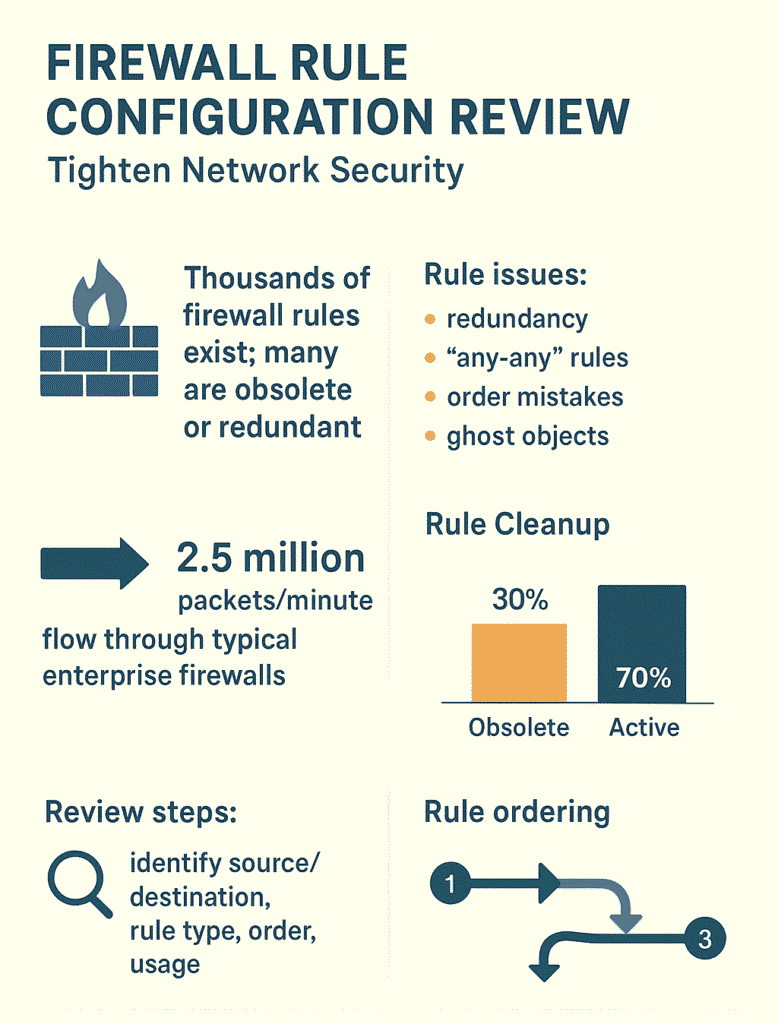
Network security lives and dies by its firewall rules. Even the fanciest hardware’s useless without solid rulesets. A typical enterprise firewall’s got thousands of rules, and they’re not all winners, some are old, some overlap, some just don’t make sense anymore.
It’s like digital spring cleaning: you’ve got to check what’s working and what’s not. Regular reviews catch those sneaky gaps that hackers love to find.
They also keep things running smooth when traffic peaks (especially during those 9 am coffee break surges). Want to learn the nuts and bolts of a proper firewall review? Keep reading.
Firewall rules are like that cluttered kitchen drawer everyone’s got, filled with stuff nobody remembers putting there. Most network admins just keep adding rules until their firewalls look worse than a high schooler’s locker at the end of the year.
Academic studies and literature reviews repeatedly call out firewall misconfiguration and rule sprawl as pervasive and hard to manage problems, finding that rule-sets are often unusable or contain anomalies that hide security risks (1).
Organizations often turn to managed firewall setups when complexity grows, since these firewall services provide more structured oversight.
It’s not like anyone plans it this way. One day you’re setting up a quick rule for some vendor access, next thing you know there’s a mess that’d make Marie Kondo cry. Here’s what’s usually going wrong behind those screens:
Most companies’ networks push about 2.5 million packets per minute through their firewalls, that’s a lot of digital traffic getting caught up in this mess. It’s like trying to direct rush hour traffic with road signs that don’t make sense anymore.
And yeah, sometimes these rules end up in a digital turf war. One says stop, another says go, and Karen from accounting can’t access her email for the third time this week.
Digging through firewall rules isn’t exactly a fun Friday night, but somebody’s got to do it. Here’s what needs checking:
And don’t even get me started on those zombie rules that just won’t die, they’re about as useful as a screen door on a submarine, just sitting there taking up space and probably causing trouble when you least expect it.
Whether it’s an allow or deny rule, overly permissive “allow” rules are a leading configuration issue; research shows rule anomalies (shadowing, redundancy, correlation) crop up frequently in real rule sets (2).

Credit: pexels.com (Photo by cottonbro studio)
Cleaning House with the Rules
That jumble of old and duplicate rules? They’ve got to go. A messy ruleset’s like trying to find your keys in a packed junk drawer, it’s going to slow you down and probably cause mistakes.
Getting the Order Right
Pretty basic stuff, but specific rules need to come first. You wouldn’t put “block all traffic” at the top of your list, right? That’s just asking for trouble. Think of it like sorting mail, the specific addresses get handled before the “current resident” catch-alls.
Matching Security Rules to Real Life
Zero trust isn’t just a buzzword anymore, it’s probably what your policy says you need to do. Rules should match what’s written down, or you might as well not have a policy at all. Simple as that.
Finding the Dead Weight
Those old IP addresses and services nobody uses? They’re like leaving your spare key under the mat, just asking for trouble. Time to clean those out, especially since most networks change about 30% of their services yearly.
Closing the Gaps
Anti-spoofing rules, blocking dangerous services, and having a solid “deny all” at the end, these aren’t optional anymore. Think of them as your network’s deadbolts. Without them, you’re basically leaving the door unlocked.
Most network folks stare at their firewall rules like they’re reading ancient hieroglyphics. There’s a better way to handle these digital barriers, and it doesn’t require a PhD in cybersecurity.
Getting Started (Without Losing Your Mind) First up, grab that mess of rules and get them somewhere you can actually see them. It’s like cleaning out a junk drawer, you’ve got to dump everything out before you can sort it. No documentation? That’s like trying to navigate Manhattan with a map of Chicago.
The actual review’s pretty straightforward:
Documentation’s a pain but skipping it is worse. Write down what changed, when it changed, and why your future self will thank you. And for heaven’s sake, automate the regular checks. There’s no reason to do this manually every time.
Nobody wants to deal with a mess of confusing rules. Here’s what works:
Real talk: good firewall rules shouldn’t need a team of experts to understand them. They should just work, stay current, and not make everyone hate their life when something needs to change.
The point isn’t perfection, it’s having rules that protect the network without turning into a full-time job. Sometimes that means being practical instead of perfect.

Credit: pexels.com (Photo by Tima Miroshnichenko)
Five mistakes that seem to pop up in every network, no exceptions:
Nobody’s got time to check thousands of rules by hand anymore. That’s where automation comes in:
And here’s the thing, when you’ve got firewalls spread across different sites, having one system watching all of them just makes sense. The machines handle the boring stuff while the security team works on actually making things better.
Those automated tools won’t replace a good network engineer’s brain, but they’ll sure make their life easier. Sometimes it’s nice to let the computers do what they’re good at.
Network security doesn’t need to be rocket science. Watching the IT team at Johnson & Greene scramble through 3,000 firewall rules last week (trying to figure out why their payment system stopped working) made this painfully clear.
Your firewall rules shouldn’t look like your grandmother’s attic. They probably do though, most networks are cluttered with digital dust bunnies that nobody’s touched since Obama was president.
Look, here’s the real deal about cleaning up those rules:
Sure, some consultant might try selling you a $15,000 automation package that promises to solve all your problems. Don’t buy it. Unless you’re running something massive like a Fortune 500 company, Excel and a few hours of focus will do just fine.
Pick a slow afternoon, maybe Friday when everyone’s thinking about the weekend. Spend 45 minutes going through recent changes. Make it a habit, like taking out the trash.
These messy rules are basically digital doors that might be hanging wide open, and you won’t know until it’s too late. Clean them up now, while you still can. Pretty basic stuff, really. It might be boring, but it beats explaining to your boss why customer data is showing up on some hacker forum.
Over time, firewalls collect redundant, outdated, and poorly ordered rules that slow performance, create security gaps, and cause operational headaches. Cleaning them up,removing unused rules, aligning them with policy, ordering them correctly, and documenting changes,prevents attacks and avoids downtime.
The article stresses that you don’t need expensive tools to do this well: consistency, discipline, and a practical review process are enough for most organizations. Make firewall reviews a routine habit, like taking out the trash,boring maybe, but far better than explaining a preventable breach later.
Partner with our experts to streamline your firewall management and strengthen security.
We offer expert consulting tailored for MSSPs to help streamline operations, reduce tool sprawl, and boost service quality.
From vendor-neutral product selection and auditing to stack optimization and decision support resources, we guide you in choosing the right tools, improving integration, and enhancing visibility.
With over 15 years of experience and 48K+ projects completed, our services include needs analysis, vendor shortlisting, PoC support, and clear, actionable recommendations,so you can build a tech stack that aligns with your business goals and operational maturity.
A firewall rule review checks if each rule still makes sense, while a firewall configuration audit looks at the bigger picture of how those rules fit into overall security. Together, they highlight gaps or weak spots.
A firewall security policy review ensures the rules reflect the actual security goals. Firewall rule validation confirms that each rule does what it’s supposed to. Firewall rule management then handles updates, removals, and approvals to keep the rules accurate over time.
Firewall rule ordering matters because rules are read in sequence, and mistakes can open or block traffic by accident. Identifying firewall unused rules helps reduce clutter and improve firewall rule performance. Both are part of a firewall audit process that looks at efficiency, accuracy, and overall health of the ruleset.
Firewall policy enforcement makes sure rules follow security requirements. Checking firewall rule compliance ensures rules meet standards. Along the way, admins must watch for firewall rule conflicts or firewall rule redundancy that can create confusion or open gaps.