Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

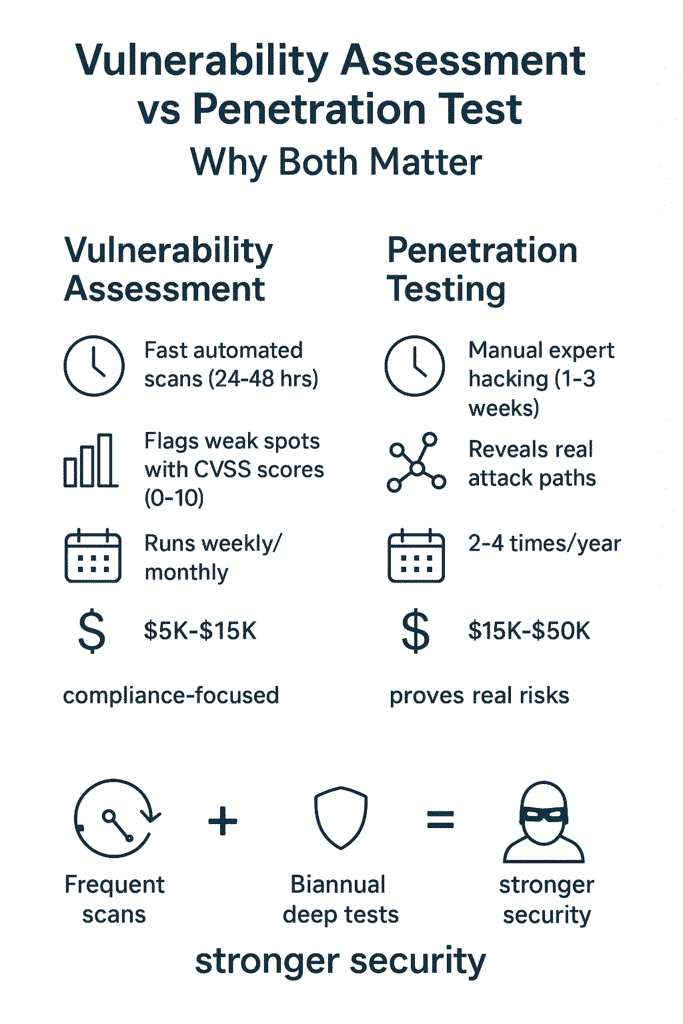
A quick scan won’t catch everything that’s wrong with your network, and that’s where the real difference lies. Think of vulnerability assessments as your annual check up , they’ll spot the obvious problems, run through a checklist of known issues (usually in about 24-48 hours).
But pen testing? That’s more like stress,testing your heart. A team of experts might spend weeks trying to break in, using the same tricks as actual hackers. Most companies need both, but knowing which to use when could save your network , and your budget. Want to know which one you need right now?
Think of vulnerability assessment like a digital health check up, where automated scanners act like security doctors checking your IT systems for weak spots.
It’s basically a bunch of smart programs combing through networks looking for problems , outdated software that’s collecting dust, systems that aren’t set up right, or patches that someone forgot to install (probably that one guy from IT who’s always on vacation).
These scanning tools crawl around your digital infrastructure like determined spiders, matching what they find against massive databases of known issues (CVE’s the big one everyone uses).
Many organizations now strengthen this process with ongoing vulnerability management programs that make sure fixes don’t slip through the cracks.
And they’re quick about it too, processing thousands of devices in the time it’d take a human to grab coffee and check their email.
The whole point here’s getting a bird’s eye view of your security situation, not diving into the weeds of how hackers might break in. What you end up with is basically a prioritized to do list of problems to fix, ranked by how much trouble they could cause.
The scoring system they call CVSS (Common Vulnerability Scoring System) helps figure out which fires to put out first. CVSS assigns vulnerability severity on a 0-10 scale, with 10 being the most critical, and includes base, temporal, and environmental metrics to provide more nuanced risk context (1).
Most places run them pretty regularly, weekly or monthly’s pretty standard. Makes sense when you think about it, since new security holes keep popping up faster than teenagers on TikTok.
There’s something seriously valuable about knowing where your weak spots are before someone else finds them. These assessments give security teams a fighting chance at staying ahead of problems, instead of always playing catch up after something’s already broken.
The scans also help keep the suits happy by checking off those compliance boxes (which nobody really loves dealing with, but hey, it’s part of the job). While they won’t show you exactly how a hacker might break in, they’ll definitely point out the unlocked doors and broken windows they’d probably try first.
Vulnerability scanning as a cornerstone IBM confirms that vulnerability scanning helps organizations catch and close weaknesses before attackers can weaponize them, and continuous scanning is a cornerstone of effective cybersecurity practice (2)
Think of penetration testing as the digital equivalent of hiring someone to break into your house , but with permission. It’s what happens when skilled hackers (the good kind) try to break into computer systems to find weak spots.
They don’t just point out problems, they actually show how bad guys might string together different attacks to cause real damage. And yeah, everyone calls it “pen testing” because who’s got time for the full phrase?
Most testing tools just scan for problems, but pen testing is different. These experts get their hands dirty, trying every trick in the book , from sneaking through networks to stealing data.
Sometimes they’ll even try social engineering, which is a fancy way of saying they’ll try to trick employees into giving up passwords or access. In many cases, companies also complement this with strong EDR solution deployment to help detect when these simulated break-ins uncover real threats.
This isn’t a quick fix kind of thing. A real pen test might take anywhere from 3 to 8 weeks (sometimes longer if we’re talking about huge companies).
The testers follow a game plan: first they scout things out, then they look for weak spots, then they try to break in, and finally they see how much damage they could do.
When it’s all done, you get this super detailed report. It’s not just some list of problems , it tells you exactly how they broke in, what they could access, and what kind of mess a real attacker could make.
It’s like getting a play-by-play of how your security actually works (or doesn’t) when someone’s really trying to break it.
Here’s the thing about pen testing , it finds stuff that regular security scans don’t catch. Like, sometimes there’s nothing wrong with individual parts of a system, but when you put them together, there’s a problem. It’s like having a bunch of locked doors but leaving a window open upstairs.
Companies usually want pen tests done before big security audits, or when they’re making major changes to their systems, or after they’ve found some scary vulnerabilities. It helps them figure out where to spend their security budget , because let’s face it, you can’t fix everything at once.
The whole point is knowing which problems could actually hurt you versus which ones just look bad on paper.

Credit: pexels.com (Photo by picjumbo.com)
Think of how campus security does those quick walks through dorm buildings checking doors and windows. That’s what vulnerability assessment feels like, fast and routine.
Pen testing? More like that one detective who hangs around asking weird questions and trying to break into buildings at 3 AM to test the alarm system.
Most vulnerability scanners finish their job in about an hour (give or take), spitting out reports while the security team grabs coffee. Meanwhile, pen testers are hunched over their laptops, manually poking at systems, probably living off energy drinks.
Vulnerability scans are pretty quick , you could scan a decent,sized office network while watching an episode of The Office. They’ll tell you if something’s obviously wrong, but don’t expect deep insights.
Pen testing’s messier and takes forever. Like, seriously forever. These guys might spend a whole week just trying different ways to crack into one system. Sometimes they’ll waste three days going down a rabbit hole that leads nowhere , but that’s kind of the point.
The scanner drops a bunch of lists and charts on your desk , here’s what’s broken, here’s how bad it is, here’s what you should fix first. It’s boring but necessary, like doing your taxes or checking your tire pressure.
Pen test reports read more like crime novels. They’ll tell you stuff like “we got into your network through a printer, stole admin passwords from a Post it notes, and could’ve wiped out your entire customer database.
Companies usually want these before launching something new or when the boss starts worrying about hackers.
Running just vulnerability scans is like only locking your front door but leaving windows open. And only doing pen tests? That’s like hiring a security guard who comes by twice a year.
You need both , run those scans every few weeks to catch obvious stuff, then get the pen testers twice a year to try breaking everything. That way you’re not just collecting lists of problems , you’re actually finding out which ones could get you in real trouble.

Credit: pexels.com (Photo by Vlada Karpovich)
A recent scan showed 47 outdated programs and way too many open ports just sitting there on the network, like windows left open in a bank. The scan spit out these CVSS numbers (kind of like a 1,10 danger score), which meant the IT folks could knock out the really bad stuff first. It made perfect sense.
Running those scans with actual login credentials , you know, the kind that let you peek under the hood , caught stuff that’d never show up otherwise. Things like a messed up admin password policy that’d been wrong for months, probably.
There’s this case where pen testers sent out fake emails that looked exactly like Microsoft password resets. They got something like 40% of employees to click through, handed over their passwords, the whole thing.
From there, these testers just walked right into the network, all the way to where the company kept their financial records. Not great.
Another time, testers found this hole in a company’s website (some Java thing that hadn’t been updated since forever), got themselves admin access in about 20 minutes flat. Really showed how one missed patch could blow the whole thing wide open.
Most places run these vulnerability scans pretty much non, stop now , weekly’s pretty common, monthly if they’re taking it easy. But the real pen testing stuff? That’s more of a special occasion thing, maybe every 3,6 months, or right before rolling out something big.
For day-to-day defense, organizations also use tools designed to contain endpoint threats quickly, bridging the gap between regular scans and deeper tests.
Works out pretty well that way. The scanning catches all the day-to-day stuff that pops up, while the pen testing makes sure everything’s actually working like it should.
When those vulnerability reports come in showing problems, teams can jump on fixes pretty quick , new patches, tweaked settings, that kind of thing. The pen testing results? That’s where companies figure out where to spend the big money , new security tools, better training programs, that sort of thing.
It’s like a constant loop: find the weak spots, test them out, fix what’s broken, repeat. Keeps everyone on their toes, that’s for sure.
Security teams have two tools at their disposal, each with its own place in the toolkit. Most people think they’re the same thing, but that’s not quite right. Here’s what makes them different and why you probably need both:
Vulnerability Assessment
Penetration Testing
The smart move? Use them together. Run those quick vulnerability scans to catch the obvious stuff, then bring in pen testers to dig deeper where it counts. That’s what the top companies do, and there’s a reason for it. Simple as that.
Some smaller companies might think they need to pick just one, but that’s missing the point. They work better as a team, like having both a metal detector and an expert locksmith checking your security. One finds the problems, the other proves they’re real.
At the end of the day, vulnerability assessments and penetration tests aren’t competing services,they’re complementary. A vulnerability assessment gives you the speed, coverage, and visibility to keep up with constant new threats.
Relying on just one leaves gaps,regular scans without validation create blind spots, and infrequent pen tests without ongoing visibility let new weaknesses slip by.
The strongest security strategies combine both: frequent vulnerability assessments to stay ahead of obvious issues, and scheduled penetration tests to stress-test defenses under real-world conditions.
Whether you’re a small business watching the budget or a large enterprise protecting critical data, the right mix of both is what turns cybersecurity from reactive firefighting into proactive resilience. In short: scans find the cracks, pen tests show the consequences,and together, they keep your organization safer.
👉 Learn how our expert consulting can help you strengthen your security stack and services. With 15+ years of experience and 48K+ projects completed, we provide tailored guidance for MSSPs to streamline operations, reduce tool sprawl, and boost service quality.
A vulnerability assessment looks for security weaknesses with tools like vulnerability scanning and vulnerability assessment programs. Penetration testing goes further with exploit simulation and attack simulation to see how far an attacker could get.
Ethical hacking is central to penetration testing methodologies. Penetration tester skills, penetration testing certification, and penetration testing ethics guide how testers safely run penetration test phases, set penetration test objectives, and deliver penetration testing reports.
A security audit, compliance testing, and vulnerability assessment compliance often work together. Penetration testing industry standards, penetration testing case studies, and vulnerability assessment frameworks help teams align with regulations.
Vulnerability assessment frequency and vulnerability scan frequency depend on how often systems change. Penetration test scheduling must account for penetration testing risks, penetration testing limitations, and penetration testing benefits.