Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

Every second counts when malicious code breaks through security. Network attacks spread faster than office gossip, turning one infected computer into a digital disaster before anyone notices.
The numbers paint a rough picture, companies take 6 hours to spot breaches while attacks need just 17 minutes to spread. That’s not great math.
Money talks though. Quick responses (under 30 minutes) save organizations around $1.2 million in cleanup costs. Most companies don’t move that fast, and their bank accounts show it. Want to know what makes the difference between quick and costly responses? Keep reading.
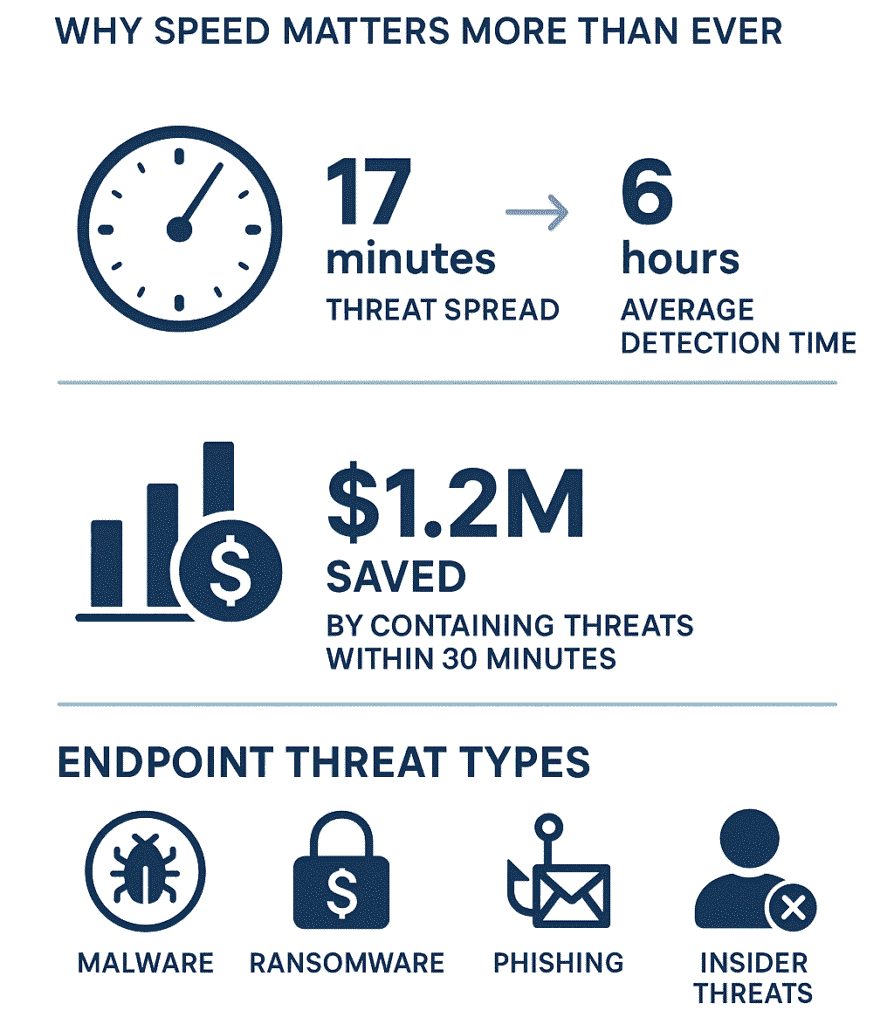
Endpoint threats are a big deal today. Many devices connect to the internet in offices, homes, and schools. Each device can be a door for bad guys to sneak in. Think about your computer, tablet, or phone. If they are not safe, they can let attackers in.
This can lead to losing important data or money. It’s scary, right? In this article, we will look at different types of endpoint threats, how attackers can get in, and why it matters. Keep reading to learn more about protecting your devices.
Malvertising (malicious ads), deceptive phishing emails, infected USB/removable media, weak or reused passwords, open remote access protocols (e.g., RDP), and insecure IoT devices are all major threats to endpoints (1)
Nobody wants to admit it, but those laptops and phones we can’t live without? They’re like open doors if we’re not careful. Here’s what’s out there:
Bad guys don’t need to break down the front door anymore, they’ve got plenty of ways in:
According to IBM’s Cost of a Data Breach Report, phishing is the most common initial breach vector, accounting for around 15% of all breaches, with phishing-related breaches costing an average of USD 4.88 million each (2).
The aftermath isn’t pretty, and numbers don’t lie:
The whole thing’s like watching dominoes fall, one compromised endpoint can bring down an entire network in hours, sometimes minutes.

Credit : pexels.com (Photo by Antoni Shkraba Studio)
Anyone who’s worked with computers knows threats move fast. Like really fast. A single infected laptop can bring down an entire network in minutes, and that’s exactly why security teams need solid plans to box in these threats before they spread.
Think of endpoint threats like a bad case of food poisoning in a restaurant kitchen – you’ve got to quarantine the problem before it affects everyone else.
When a device gets compromised, the goal’s pretty straightforward: isolate it, stop the spread, and keep everything else running while you figure out what went wrong.
Smart teams use these tried-and-true methods:
Most organizations see their response times drop from 3-4 hours down to just 2-3 minutes (and sometimes even faster) with good automation.
Here’s what you’ll need in your digital medicine cabinet:
The proof’s in the numbers:
Good teams track these stats religiously, always pushing to shave off seconds and minutes from their response times.

Credit: pexels.com (Photo by Tima Miroshnichenko)
The clock never stops in cybersecurity. Every second counts when malware’s spreading through a network like wildfire, making rapid EDR incident investigation essential to containing the damage. That’s just how it is these days.
A few things really make the difference:
Some pretty annoying roadblocks keep popping up:
Here’s what’s making a real difference:
These changes aren’t just theory, they’re cutting detection time down from days to hours, sometimes even minutes. Pretty huge when you think about it.
The old school approach of watching security monitors doesn’t cut it anymore. The real power comes from getting security tools to cooperate, sharing data in ways that catch the bad guys before they wreak havoc.
These days, threat feeds work like a neighborhood watch on steroids. When something suspicious pops up, machine learning spots it faster than any human could, catching those subtle patterns that even the most caffeinated analyst might miss.
Stack these systems together and you’re looking at defense that actually works.
The smart security teams don’t just sit there waiting for alarms. They’re digging through logs at 2 AM, finding the breadcrumbs that point to trouble. A client’s team cut their response time from 6 hours (practically a lifetime in security) down to 45 minutes by staying on the offensive.
XDR’s changed everything about how teams spot trouble. It watches the endpoints, networks, and every email that moves through the system.
When something happens, you don’t just see bits and pieces , you get the whole story laid out in front of you. Most teams used to spend half their day piecing together what EDR management now shows in seconds.
The numbers don’t lie:
Average incident costs dropped 47% when teams cut response times below the one-hour mark. That’s real money saved, not just theoretical benefits.
Speed really tells the story when it comes to stopping threats at the endpoints. Just spotting problems doesn’t cut it anymore, security teams have to lock down threats, figure out what’s happening, and clean up the mess faster than the bad guys can work.
Most of the heavy lifting gets done through machines now (AI handles a lot of the analysis), while threat data and active searching for risks helps cut down reaction time. If your security group’s taking too long to shut down endpoint attacks, you’ve got to switch things up.
Start by taking a hard look at your security tools, find spots where computers could do the work, and get your different security teams talking to each other. Quick containment isn’t some fancy goal to shoot for; it’s what keeps your company’s data safe, your name clean, and your business running.
That’s where expert guidance makes all the difference. We help MSSPs streamline operations, reduce tool sprawl, and improve service quality with vendor-neutral product selection, stack optimization, and actionable recommendations.
With 15+ years of experience and over 48,000 projects completed, we know how to align your technology and teams for faster detection, containment, and recovery. Get expert guidance and strengthen your endpoint defenses today.
Endpoint threat containment is about stopping an attack before it spreads, while faster threat containment focuses on cutting down reaction time. By using automated threat containment and endpoint incident response, teams can act the moment rapid endpoint threat detection spots something unusual.
When attackers get inside, they often move across systems to widen access. Endpoint lateral movement prevention stops this spread, while endpoint privilege escalation blocking limits the attacker’s control. Combined with network segmentation for endpoints and endpoint attack containment.
Endpoint forensic investigation uncovers what happened, why, and how, which helps teams make sense of incidents. This evidence drives endpoint threat triage, showing which issues matter most. Automated threat remediation then fixes problems faster, guided by forensic findings.
Endpoint malware blocking and endpoint attack containment work best when tied to endpoint security orchestration. Orchestration connects automated workflows like endpoint incident investigation, endpoint attack surface reduction, and endpoint dwell time reduction.