Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

When cyber attackers settle into a network unnoticed, the damage piles up fast. Our experience tells us that the longer they stay, the more data they steal, the deeper they move sideways, and the harder they are to evict.
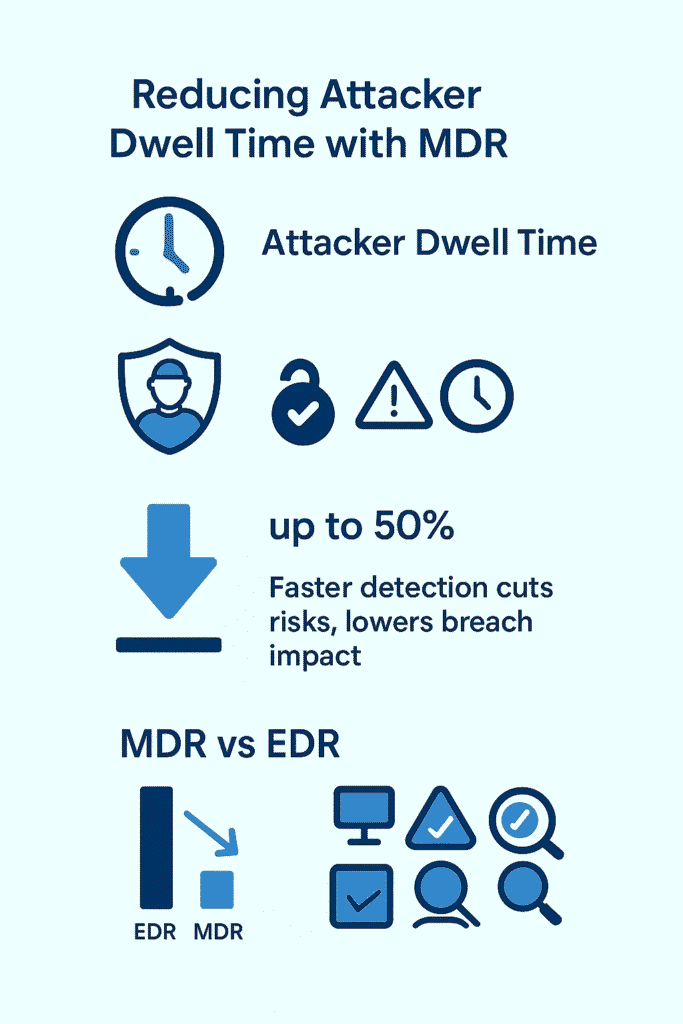
Reducing attacker dwell time , the span attackers remain hidden , is a key defense line. Managed Detection and Response (MDR) offers a way to shrink that window from weeks or months down to hours or days, changing the security game for organizations struggling with stealthy threats.
Hidden in networks across the globe, cyber attackers slip through defenses and make themselves at home. That’s dwell time , the span between an intruder’s first step into a system and when someone finally spots them.
We’re talking weeks, sometimes months of unauthorized access that security teams don’t even know about. These digital squatters don’t just camp out doing nothing. Day after day, they crawl through systems, plant hidden doorways, and steal whatever data catches their eye.
It’s kind of like termites in a house , the longer they stay, the more structural damage they do. A few days of dwell time might mean a quick cleanup. But months? That’s when things get messy.
The attackers have had time to spread everywhere, grab admin rights, and cover their tracks so well it’s nearly impossible to trace their path.
And yeah, that means the recovery’s gonna hurt , both the wallet and the reputation. The math isn’t complicated: less time inside means less chance to wreck things. But too many companies still don’t catch on quick enough, and they pay for it. Big time.
And when organizations use advanced tools like AI-powered detection, the reduction is even more dramatic. AI-enabled systems can cut dwell time by 74%, and incident response costs by 42% (1).
Managed Detection and Response (MDR) steps up to cut that dwell time down. Think of it as a 24/7 security operation that’s always watching, always ready to jump on threats.
Organizations that take time to understand different MDR service levels see how each level shapes the speed and depth of protection.
The speed here’s impressive, we’re talking near instant detection in most cases. MDR uses a mix of smart endpoint tools (the tech that watches each computer), threat intel (what’s happening in the wider cyber world), and actual human analysts who know what they’re looking at.
Can’t just rely on computers to sort out what’s dangerous and what’s not , you’d drown in false alarms.
When MDR spots something fishy, it moves fast:
The whole system runs on five main engines:
The tech’s great, but it’s the human touch that makes MDR work. Those analysts don’t just sit around waiting for alarms, they’re actively hunting through systems, connecting dots most people wouldn’t see.
This mix of people and technology highlights what managed detection response is really about, blending nonstop monitoring with quick action.
For companies that can’t afford massive security teams (and let’s be honest, that’s most of them), MDR fills a crucial gap. Instead of weeks wondering if someone’s lurking in their network, they get answers in hours. Sometimes minutes.
The numbers don’t lie, organizations using MDR cut their dwell times down from months to days. In the cyber world, that’s the difference between a minor headache and a full, blown crisis.
Most companies can’t keep up with basic cybersecurity needs these days. They’re flying blind in their networks, can’t find enough experts to hire, and take way too long to check their alerts. No MDR means attackers get to hang around longer, much longer.
In the real world, breaches often go unnoticed for weeks (sometimes 30+ days). Bad actors use this time to sneak around systems, grab admin privileges, and steal whatever they want. By the time anyone notices, the damage is done: systems down, money lost, and customers losing faith fast.
It’s pretty much impossible to cut down these attack times without the right tech and people watching the shop.
The moment companies switch to MDR, things change. They catch the bad guys early, before they can do real damage. Breaches hurt less, and containing them becomes way more manageable.
These MDR benefits are clear, faster detection, stronger defenses, and smoother compliance all in one package.
Security teams see this improvement right away. Round the clock monitoring and quick responses help build stronger defenses against the constant stream of threats, while closing off weak spots that attackers love to exploit.
Plus, MDR makes those dreaded compliance checks easier by documenting everything and keeping threat intel current , exactly what auditors want to see.

Credit: unsplash.com (Photo by Ales Nesetril)
Here’s how MDR cuts down the time attackers spend in systems:
MDR uses some pretty sophisticated tech (like SIEM and XDR) to watch everything , endpoints, networks, cloud stuff. All this data feeds into systems that filter out the noise and point to real threats.
This means teams don’t waste time chasing false alarms. They spot break ins within hours, sometimes minutes, instead of weeks.
IBM defines MDR as a 24/7 real-time cybersecurity service, combining automated tools with expert analysis to rapidly detect and respond to threats across an organization’s entire infrastructure, covering networks, endpoints, and the cloud (2)
When something sketchy pops up, automatic response kicks in , quarantining infected machines, killing bad processes, locking out compromised accounts. Meanwhile, analysts double, check everything and fine tune the response.
Mix smart machines with smart people, and attackers don’t stand a chance of spreading through the network.
MDR doesn’t clock out at 5. It’s always watching, making sure threats don’t come back or try new tricks. After each incident, forensics teams dig deep to figure out exactly what happened.
This never ending cycle of watching, learning, and improving keeps pushing those attack times down, making the whole system tougher to crack.
MDR security teams bring a human touch that EDR tools just don’t have. Think of EDR as a security camera , it’ll show you what’s happening, but someone’s got to actually do something about the break-in.
MDR’s the complete package, with real people watching and ready to jump in (usually within 15,30 minutes of detecting something fishy).
The numbers don’t lie, attackers hang around for an average of 207 days without MDR services. That’s seven months of potential damage. Companies using MDR cut that down to about 24,72 hours max.
More businesses are catching on, with MDR adoption up 300% since 2019, and it makes sense considering how crafty these cybercriminals have gotten.
A manufacturing company’s MDR team caught attackers trying to spread ransomware at 2 AM on a Sunday. Within 20 minutes, they’d locked down the affected machines and stopped the attack cold. No ransom paid, minimal cleanup needed.
That’s the kind of speed you just don’t get with basic EDR tools sitting there waiting for someone to check the alerts.
When you kick intruders out faster, you get:
And here’s the thing , every hour counts. The difference between catching something in 2 hours versus 2 weeks isn’t just numbers on a spreadsheet, it’s the difference between a minor incident and a major breach that ends up in the news.
Cutting down the time hackers spend inside networks stands out as one of the most effective ways to stop data theft. Watching security teams work around the clock showed how blending 24/7 system checks, smart analysts, and quick, trigger defense tools cuts attack windows from months to hours.
Companies get wind of breaches faster, suffer less damage, and wind up with tougher defenses. Without a solid plan to catch intruders early, your company’s probably giving attackers too much room to roam. Look into managed detection teams that know their stuff , they’re worth every penny.
Each day hackers go unnoticed means more risk, so getting good at spotting and stopping them fast really matters. The math is simple: shorter attack times equal better odds of keeping your data safe while the bad guys keep hammering away.
Get started with expert detection and defense today
Attack suppression strategies slow down or block intruders. Attack behavior analysis studies how attackers move. Attack timeline compression shrinks the time frame they have to act.
Together, these improve attacker dwell time metrics, giving defenders a clearer view of progress and showing how security efforts cut the time hackers linger.
Attack surface reduction lowers the number of open doors. Attack surface visibility shows which systems are exposed. Vulnerability exploitation timing reveals when attackers strike weaknesses.
For defending critical infrastructure, these work together to close gaps and prepare defenders to react before attacks cause serious harm.
A strong cyberattack response workflow ensures teams act in order. Incident response automation speeds up steps that once took hours. Post-breach remediation restores systems and closes holes.
Together, they focus on minimizing breach impact and reducing cyber incident impact, keeping recovery times shorter and damage under control.
Anomaly detection systems flag unusual behavior. Security alert reduction clears noise so real risks stand out. Forensic incident analysis explains how attacks unfold.
Combined with threat containment protocols, these measures improve cybersecurity detection metrics, showing defenders where they succeed and where attackers still slip through.