Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

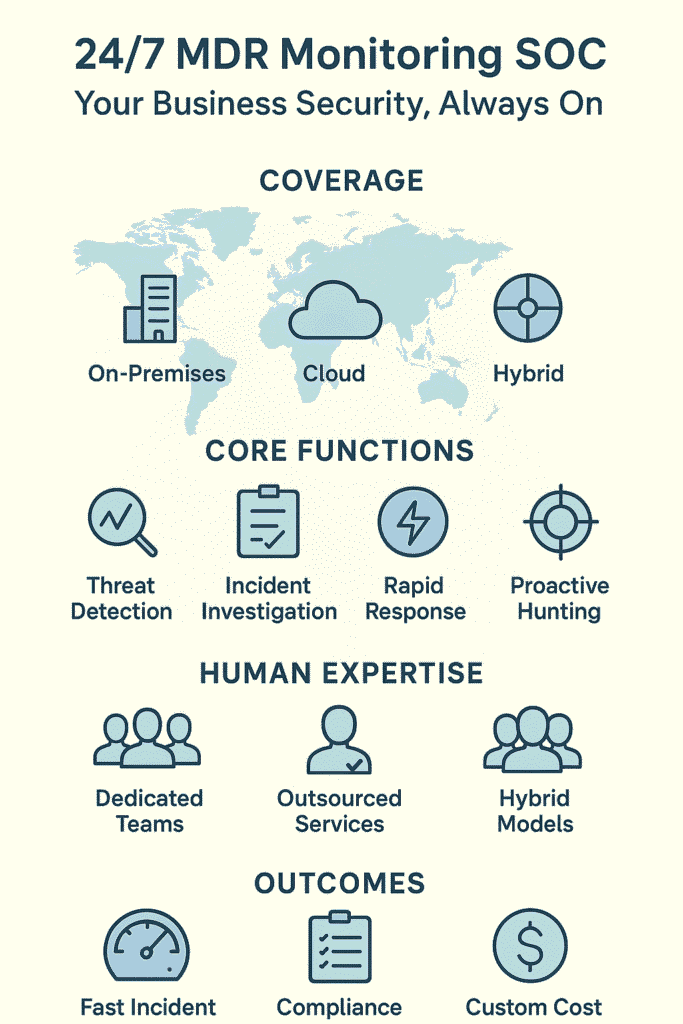
Night after night, security analysts stare at screens filled with endless streams of data, watching for that one anomaly that could signal trouble. Their vigilance represents the front line of modern cybersecurity , the 24/7 MDR monitoring SOC that never stops working.
The digital landscape’s gotten pretty scary lately, with attacks happening at all hours. That’s exactly why these round-the-clock security operations centers have become such a necessity. They’re constantly on guard, watching networks, computers, and cloud systems for anything that looks off.
The real power here isn’t just in the fancy computer systems (though they’re pretty impressive). It’s in how human expertise and smart technology work together, kind of like a well, oiled machine that spots and stops threats before they can do real damage.
For companies trying to stay safe in today’s digital world, this non, stop watchdog service might just be their best friend.
In the basement of a nondescript office building, screens cast an eerie blue glow across tired faces. Coffee cups, litter desks, and keyboards click steadily as analysts track digital threats across countless networks.
Welcome to the heart of a 24/7 MDR Monitoring SOC, where sleep isn’t really part of the job description.
Let’s face it , most companies still run on old iron. Those beige server boxes might not be pretty, but they’re keeping businesses alive. SOC teams plug into these networks, watching everything from ancient print servers to spanking, new workstations.
And yeah, they’ve seen it all: forgotten test servers still running Windows Server 2003, network closets that haven’t been opened since Obama’s first term, and printers that probably qualify for social security .
Meanwhile, 44% of mission critical components, like servers and storage networks, are still based on legacy infrastructure, pointing to the slow pace of modernization (1).
The cloud’s a different beast altogether. Between AWS eating credit cards for breakfast and Azure throwing random errors at 2 AM, SOC teams don’t get much rest.
They’re watching for the weird stuff , like that one developer who keeps trying to spin up Bitcoin miners in us,east,2, or those suspiciously chatty containers in your Kubernetes cluster.
Nobody’s running pure anything anymore , it’s all mixed up. Some data lives in the cloud, some stays home, and SOC teams get to watch it all bounce back and forth. It’s like herding cats, if the cats were carrying sensitive company data and had a habit of hiding in dark corners.

Credit: unsplash.com (Glenn Carstens-Peters)
The tools aren’t cheap, but neither is getting hacked. SOC analysts swim through oceans of data (we’re talking terabytes per day), while AI helps spot the nasty stuff.
There’s always some new acronym to learn , SIEM, EDR, XDR , but they all do one thing: catch bad guys. For many businesses, understanding MDR service levels has become key to deciding how deep this protection should go.
Machines are smart, but humans still run the show. The analysts (running on a diet of energy drinks and takeout) dig through alerts like digital archaeologists. They’re looking for patterns, connecting dots, and figuring out if that login from North Korea is really just the CEO on vacation.
Even when automation is in place, human teams remain essential. Organizations with AI and automation in place experienced 108-day shorter breach lifecycles compared to those without, yet this still depends on analysts interpreting the results (2).
When things go wrong, they go wrong fast. Good SOC teams move faster, killing malicious processes and quarantining systems before the damage spreads. No time for meetings or emails , just rapid action and quick decisions.
Sometimes waiting for alerts isn’t enough. SOC teams get creative, poking around in dark corners and checking under digital rocks for threats that slipped through. They’re always learning, always adapting, because tomorrow’s attacks probably won’t look like today’s.
Security tools don’t mean much without the right people behind them. Round the clock expert teams make the real difference between spotting an attack and missing it entirely.
Some companies run their own security operations centers, staffing them with bleary,eyed analysts who’ve probably consumed too much coffee during those 3 AM shifts. These teams (usually working in 8,12 hour rotations) spend their days swimming through alerts, digging into suspicious activity, and putting out digital fires before they spread.
Building an in-house SOC isn’t cheap , we’re talking millions in salaries and tech. That’s why many businesses turn to managed detection and response providers instead. These outside teams bring their A game without the astronomical costs, plus they’re already up and running from day one.
Sometimes the best setup is a mix of both worlds. Internal teams who know the company’s systems inside and out work alongside MDR providers who’ve seen thousands of attacks across different organizations. It’s like having local cops who know the neighborhood working with federal agents who’ve tracked criminals nationwide.
Every industry’s got its own security headaches. Hospitals worry about patient data and ransomware that could shut down vital equipment. Banks need to watch for fraud and meet strict payment security rules. Good MDR teams know these differences and adjust their hunting accordingly.
The proof’s in the numbers when it comes to 24/7 monitoring. Here’s what changes when you’ve got experts watching the screens:
The bad guys don’t stick around as long. Most threats get caught within hours instead of months, and analysts spend their time chasing real problems instead of wild geese.
This is one of the overlooked MDR benefits that helps businesses cut risk while also keeping costs in check.
When something bad happens, it gets handled fast , usually within minutes or hours, not days. Quick response means less damage and fewer angry customers calling about downtime.
SOCs help tick those regulatory boxes for ISO 27001, SOC 2, and all those other alphabet soup requirements. It makes audits less painful and keeps the compliance folks happy.
Most providers charge based on how much you use , could be per computer, per person, or by how many logs they process. You can usually start small and scale up as needed, so you’re not stuck paying for more security than you need.
The whole MDR thing isn’t rocket science, but it’s not exactly plug,and play either. Here’s what you’ll need to think about before jumping in:
The right MDR setup means sleeping better at night, knowing someone’s got eyes on your network while you’re catching z’s.
Cyber creeps don’t clock out at 5 PM, and neither should your security team. Good MDR monitoring brings together smart tech and even smarter people to catch the stuff that regular security might miss.
Size doesn’t matter here , whether you’re five people in a garage or 5,000 across three continents, having pros watching your back 24/7 just makes sense. If you’re thinking your security could use an upgrade (and let’s be honest, it probably could), looking into MDR should be right at the top of your to-do list.
All three terms describe watching systems for problems, but they differ in focus. 24/7 cybersecurity monitoring means nonstop coverage.
Real-time security monitoring highlights instant alerts, while IT security monitoring covers a wider scope of networks, endpoints, and applications within a SOC operations center.
These services combine people and tools to spot problems quickly. Managed detection and response or MDR services mix human analysts with automation. SOC as a service offers the same skills without building your own team.
These tools track different parts of your environment. Endpoint detection and response monitors devices, network security monitoring checks data traffic, and cloud security monitoring looks at cloud systems.
SIEM integration gathers events from many systems into one place. This supports security event management by sorting what matters most. It also improves log management, reduces noise with automated alert triage.