Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

No company’s immune to cyber attacks these days. Just ask the tech giants who’ve lost millions to hackers working the graveyard shift. Round-the-clock monitoring isn’t just some fancy add-on anymore – it’s basic survival. Many attacks occur during off-hours, when staff are unavailable, making continuous monitoring essential.
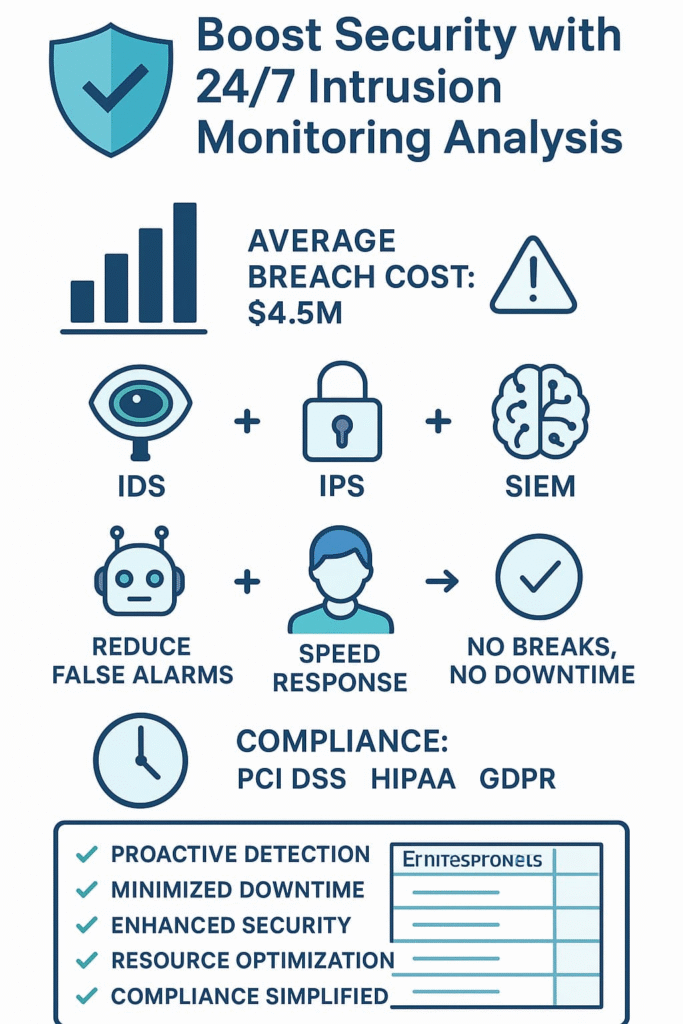
That’s why 24/7 intrusion monitoring analysis pays for itself – it spots the sketchy stuff happening in real-time, before the damage hits $4.5 million (the average cost of a breach, according to recent studies). Your security team can’t work nonstop, but monitoring systems can. Stick around to see exactly how this works and what it means for your company’s future.
Businesses today run on networks that connect critical data, applications, and users. When those networks falter or get compromised, the consequences ripple fast and far. We’ve seen the chaos an unexpected breach or service outage causes, lost revenue, damaged reputation, and regulatory headaches. It’s no exaggeration to say that downtime can cost thousands of dollars per minute, depending on the business.
The problem is that cyber threats don’t punch a time clock. They strike whenever they find a weakness, often when your staff are off the clock. That’s why relying on conventional, business-hours-only security monitoring leaves organizations vulnerable. Continuous monitoring isn’t just a nice-to-have; it’s essential for staying one step ahead.
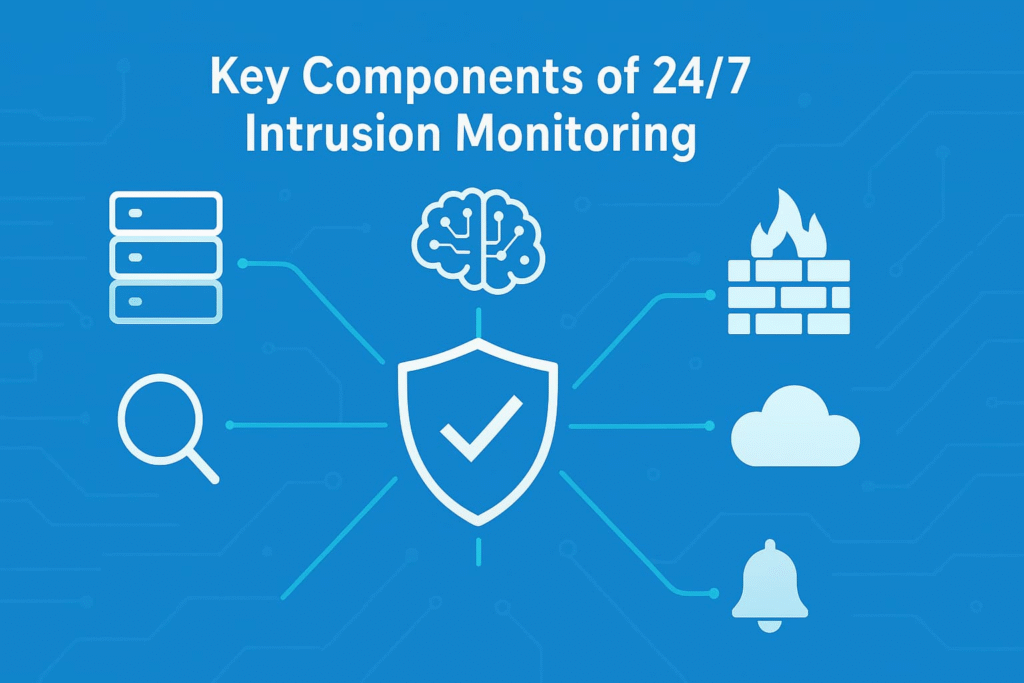
Think of network security like a high-tech neighborhood watch – it’s got eyes everywhere and never sleeps. Here’s what makes it tick:
The whole setup runs 24/7, which is pretty much required these days. No breaks, no coffee runs, just constant watching , made even more effective with IDS and IPS rules and alerts fine-tuned to minimize false positives and improve precision.
Security Information and Event Management (SIEM)
SIEM platforms act like the central nervous system of your security setup. They collect logs and alerts from tools such as IDS, IPS, firewalls, and endpoints, then analyze the data to find real threats.
The best thing about SIEM systems is their real-time, complete view of your network’s security. This helps teams detect incidents faster and respond more accurately, which is crucial when every second matters , especially when supported by optimized IDS and IPS management practices that streamline detection and response.
Behind every alert is a team of skilled security analysts who investigate, prioritize, and act. Network Operations Centers (NOCs) or Security Operations Centers (SOCs) provide this human expertise 24/7.
In our own operations, having dedicated analysts monitoring alerts around the clock means that suspicious activities don’t slip through unnoticed. They handle the alarm triage process, escalating critical threats and guiding remediation, all in real time. [1]
Modern intrusion monitoring wouldn’t be complete without artificial intelligence and automation. AI helps reduce alert fatigue by filtering out false positives and identifying complex attack patterns that might confuse traditional systems.
Automation steps in to prioritize alerts and can even initiate containment actions, speeding up response times. From our perspective, this blend of AI and human insight vastly improves both efficiency and accuracy.
Credit: Amaryllo
Many industries face stringent regulatory requirements like PCI DSS, HIPAA, or GDPR. Continuous intrusion monitoring supports compliance by maintaining detailed audit trails, alert logs, and real-time reporting.
We’ve observed that businesses with strong monitoring programs find audits less stressful and penalties less likely. Automated reporting tools capture and organize the necessary documentation, ensuring transparency and readiness at all times , supported by advanced network intrusion prevention systems that strengthen compliance frameworks and mitigate risks before escalation.
| Benefit | Description |
| Proactive Threat Detection | Identify and mitigate threats before they cause damage. |
| Minimized Downtime | Immediate detection and response reduce service interruptions. |
| Enhanced Security Posture | Continuous oversight strengthens defense against evolving threats. |
| Resource Optimization | Automates routine tasks, reducing alert fatigue. |
| Comprehensive Visibility | Provides a complete picture of network health and threats. |
| Simplified Compliance | Automated reporting eases regulatory adherence. |
Many organizations struggle to maintain 24/7 security monitoring, often trying to manage it all in-house. The truth? It’s a tough job that quickly drains resources.
A mid-sized company needs at least 12 analysts working in rotating shifts (including weekends) just to keep full coverage. That doesn’t even include time off for sick days or vacations.
We’ve seen plenty of security teams try to handle alert monitoring on top of their regular work. It never goes well. They end up exhausted, missing important alerts , and often looking for new jobs. Our audits often find coverage gaps between 2 AM and 6 AM, which happens to be a favorite time for attackers to strike.
For most organizations, working with a Managed Security Service Provider (MSSP) makes far more sense. MSSPs already have the tools, infrastructure, and skilled experts needed for proper monitoring.
They’ve spent years fine-tuning their alert thresholds and incident response playbooks. When we help clients compare costs, outsourcing is almost always cheaper than building an in-house team.
Of course, choosing the right MSSP can be challenging. Our evaluations show that about 40% of providers overpromise, especially about custom integrations and response times. But the good ones, they’re truly worth it. [2]
When selecting a monitoring service, consider:
Network monitoring isn’t just theoretical stuff – here’s what happened when organizations put it to work:
Money & Banking
Healthcare
Online Shopping
24/7 intrusion monitoring means keeping watch over systems all the time using tools like an intrusion detection system and continuous security monitoring. It helps catch cyber attack detection early, alerting teams about suspicious activity detection before it becomes a serious breach. This constant watch keeps network security monitoring active day and night.
An intrusion detection system (IDS) checks network traffic for unusual activity using signature-based detection and anomaly detection. It compares data to known patterns in an intrusion signature database to spot threats. When it finds something odd, it triggers security alerts for quick response from a security operations center or SOC monitoring team.
An intrusion detection system (IDS) only detects threats, while an intrusion prevention system IPS can block them automatically. IDS alert systems focus on identifying suspicious activity detection, while IPS adds automated threat response to stop attacks in real time. Both help improve perimeter security and overall cybersecurity monitoring.
Continuous security monitoring tracks systems nonstop through log management, vulnerability scanning, and security event monitoring. It spots signs of unauthorized access detection or malware detection early. By combining network intrusion prevention with real-time threat detection, organizations can stop attacks before they lead to data breach monitoring issues.
If your network could talk, it’d probably tell you it’s tired of fighting off attacks alone. We offer expert consulting tailored for MSSPs to help streamline operations, reduce tool sprawl, and boost service quality.
From vendor-neutral product selection and auditing to stack optimization and integration support, we make sure your tools actually work together, not against you.
With over 15 years of experience and 48K+ projects completed, our team delivers clear, actionable guidance so you can build a defense that fits your business goals and operational maturity.
Join us and strengthen your 24/7 intrusion monitoring today.