Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM

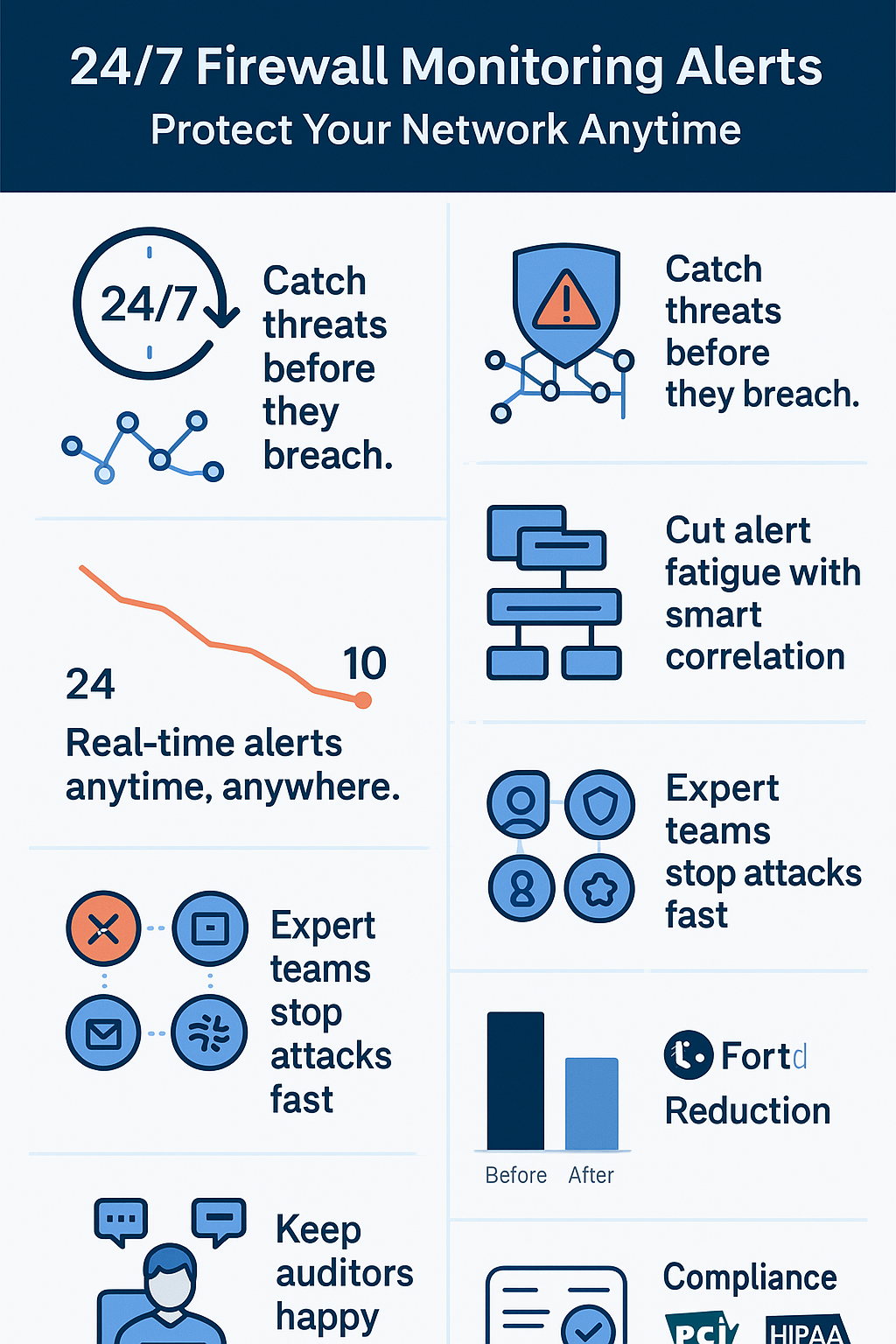
24/7 firewall monitoring alerts aren’t exactly exciting stuff, but they’re pretty much the only thing standing between your network and the bad guys out there. Every day, these alerts catch thousands of attempts to poke holes in network defenses, some dumb, some scary smart.
Maybe it’s someone trying every password combo they can think of at midnight, or that one computer in accounting suddenly talking to servers in countries you’ve never done business with. Most hackers these days are pretty sneaky about it, they don’t make much noise, just look for the smallest way in. Skip the monitoring, and you might as well post your network passwords on Twitter.
Want to know what really goes into keeping the digital doors locked? Let’s get into it.
Nobody really wants to think about network security until something breaks. Most folks running these systems will tell you it’s not about the fancy bells and whistles, it’s about catching the jerks trying to break in before they do real damage. These alert setups basically work like a night watchman who’s been at the same building for 20 years. They know when something smells funny.
The basics that keep it running:
Pretty handy how it strings things together too. Instead of bombing some poor IT guy with ten thousand alerts about the same thing, it kinda connects the dots. Like when someone’s messing around, you can see everything from their first failed password attempt to whatever they tried to mess with in the firewall rules.
The guys staring at screens all shift need to know where to look when stuff hits the fan. That’s where those network maps come in, shows exactly which part of the building’s on fire, so to speak. Sure, the computers do most of the work, but you still need real people watching (usually some mix of fresh-faced newbies and crusty old pros). Because sometimes you just know something’s wrong, even if you can’t put your finger on why.
Watching network traffic is about as exciting as watching paint dry. But that’s the point, computers don’t get bored like people do. They just sit there, day in and day out, checking every packet that moves.
With thousands of connection attempts hitting most networks every minute, it’s crucial to have threat detection monitoring in place to catch anomalies early. According to Mandiant’s M-Trends 2024 Special Report, the global median dwell time, the time it takes to detect a breach, has decreased to 10 days, down from 24 days two years earlier. [1]
The old school “block the known bad IPs” approach is pretty much useless these days. Now it’s all about catching the weird stuff, like when that forgotten server in the corner starts puking encrypted files at 2 AM, or when Bob’s account tries logging in from New York right after using it in Tokyo. Sometimes things just don’t smell right.
Finding out your network got hacked by reading yesterday’s email sucks. That’s why these things now bug you anywhere they can, your phone blows up, Slack starts pinging, Teams goes nuts. Some poor soul’s always gotta be on call, but at least they know right away when stuff breaks.
These alerts multiply like rabbits if you let them. But decent systems can tell when it’s the same person trying to guess passwords repeatedly, consolidating notifications to prevent alert fatigue. This approach is vital, as cybersecurity teams often struggle to keep up with a surge of security alerts, now taking an average of 11 person-hours to investigate each incident. [2]
Nobody likes getting spammed with the same alert fifty times. So these things learn to bundle up the repeats. When something does pop up, it’s usually got enough meat on it to actually do something about the problem.
The sneaky stuff leaves breadcrumbs all over the place. Good systems string it all together, like how that weird login led to some files getting copied, then something calling home to Russia. Gives the security folks the whole story without making them play detective.
Nobody likes digging through logs, but that’s where all the good stuff hides. Every blocked connection, every weird traffic spike, every time someone tweaks a firewall rule, it’s all in there. Mix that with the alert system and you start seeing patterns that make sense.
The visual stuff helps too, like having a map of your building where you can see exactly which doors got rattled. Some key things these logs catch:
When something does break through, you gotta figure out how they got in. Maybe someone left a port open, or that new firewall rule wasn’t as tight as everyone thought. Either way, you dig until you find the hole, then plug it before someone else finds it too.
Credits: Simplilearn
Look, most companies can’t afford to have security pros sitting around 24/7 waiting for alerts. That’s where managed firewall services come in; it’s their whole job to watch for trouble. When something pops up at midnight, you’ve got someone who knows what they’re doing already on it. In fact, the average cost of a data breach was $4.88 million in 2024, highlighting the financial impact of delayed detection and response.
These teams don’t mess around with response time. While your internal IT folks are still getting out of bed and brewing coffee, the managed team’s already blocking the attack and cleaning up the mess. For smaller shops without their own security war room, it’s pretty much the only way to go.
Plus, they don’t just fix the immediate problem, they come back with “here’s how to stop this from happening again” type stuff. Lets your regular IT people focus on keeping the lights on instead of playing cyber detective all day.
Nobody likes finding out they’ve been hacked for the past six months. With decent monitoring, you usually catch the intruders before they get past the front door. For instance, organizations following compliance requirements for 24/7 monitoring can detect anomalies much sooner, reducing the average time to identify a breach significantly.
Most tech folks didn’t sign up to stare at firewall logs all day. When the system handles the basic watching, they can actually work on stuff that moves the business forward. The compliance people sleep better too, since all those annoying audit requirements get handled automatically.
The worst calls are always about stuff being down. With proper monitoring, you catch the small problems before they turn into dumpster fires. One client cut their downtime by 60% just by catching server issues before users noticed.
As networks get bigger and messier, these systems scale up pretty nicely. You can tune the alerts so you’re not getting pinged about every little hiccup, but still catch the stuff that matters.
Sure, dashboards aren’t exciting, but they tell you if things are actually working or just look like they are. Most folks check their numbers weekly, some daily, depends how paranoid their boss is.
The faster you know something’s broken, the faster you can fix it. Had one client whose old setup meant finding out about failed firewalls when users started screaming. Now they know before anyone else notices.
Nobody likes audits, but they suck less when you’ve got all your paperwork in order. These systems keep track of everything, every alert, every response, every fix. Makes those compliance meetings a lot shorter.

Effective alerting depends on timely delivery. Systems employ multi-channel notifications to reach personnel wherever they are. SMS and email remain staples, while chat integrations with Slack or Teams offer real-time collaboration.
The incident summary includes recommended remediation steps, making it easier for teams to act without delay. Detailed incident reports provide context, helping security operations integrate alerts into broader workflows.
This integration is critical. Alerts form the cornerstone of security operations, enabling continuous coverage that never sleeps.
24/7 firewall monitoring keeps constant watch on your network perimeter with real-time monitoring and intrusion detection to spot unauthorized traffic or suspicious activity. By combining firewall logs, packet filtering, and traffic analysis, it flags security alerts and sends automated alerts when policy violations or unauthorized access attempts occur.
This proactive monitoring helps with data protection, breach notification, and ensures compliance monitoring by enforcing firewall rules and rule optimization.
If a firewall appliance goes down after business hours, a high availability setup ensures uptime monitoring and continuous surveillance with a backup device. Managed firewall services with SOC monitoring and remote monitoring keep event logs flowing, maintain firewall configuration, and alert escalation triggers.
This defense in depth approach limits downtime, prevents malicious traffic, and keeps security event management active for incident response even when IT staff is offline.
Security operations center teams collect firewall logs, correlate event logs with SIEM tools, and run network forensics to pinpoint suspicious activity or anomalies. Using firewall analytics, log management, and TCP/IP monitoring, they perform root cause analysis and alert prioritization.
The escalation workflow makes sure the right team sees alert notifications quickly, helping incident response teams apply security best practices and reduce risk from external threats or insider threats.
Next-gen firewall appliances support encrypted traffic monitoring using rule enforcement and policy compliance controls. They analyze traffic patterns for anomaly detection without decrypting sensitive data unnecessarily.
Firewall dashboards show operational visibility and firewall reporting that highlights policy violations or unauthorized traffic, ensuring compliance monitoring and IT security standards. This approach balances network security, data protection, and zero trust security while still allowing for adaptive response to threats.
Integrating SIEM tools with firewall change management provides centralized security event management and better operational visibility. Log correlation and alert thresholds become consistent across systems, and security automation speeds up response to suspicious activity.
Multi-channel alerts reach IT security teams quickly, while cloud firewall rules and firewall audit data stay synchronized. This integration supports risk assessment, attack prevention, and managed service provider workflows for proactive monitoring and defense in depth.
Continuous 24/7 firewall monitoring alerts strengthen network defense by providing real-time detection, reducing noise, and offering rich context through logs and visual models.
Expert-managed services deliver alerts across multiple channels, ensuring no threat goes unnoticed. IT teams gain relief from constant manual monitoring while focusing on stopping attacks. Transform your cyber security posture and get peace of mind every hour, every day.
Learn how MSSPs can optimize their security stack here.